Public key authentication in PuTTY removes routine password entry when connecting from Windows to remote SSH servers, improving security and making repeated administrative logins faster. It also reduces exposure to password guessing attacks because no reusable password needs to cross the network during login.
SSH public key authentication works by placing a user's public key on the server (in the account's authorized_keys file) while keeping the matching private key on the client. During authentication, the server verifies proof of possession of the private key without ever receiving it, and PuTTY supplies that private key from a .ppk file selected in the session settings.
Server-side configuration and key handling still matter for a successful login. Public key authentication must be enabled on the OpenSSH server, the correct username must be used, and host key prompts should only be accepted after the fingerprint is verified to avoid man-in-the-middle risks.
Steps to use public key authentication in PuTTY:
- Create a public and private key pair in PuTTYgen if a key pair is not already available.
- Copy the public key to the server account's authorized_keys file.
The file is typically located at /home/username/.ssh/authorized_keys on Linux servers.
- Launch PuTTY.
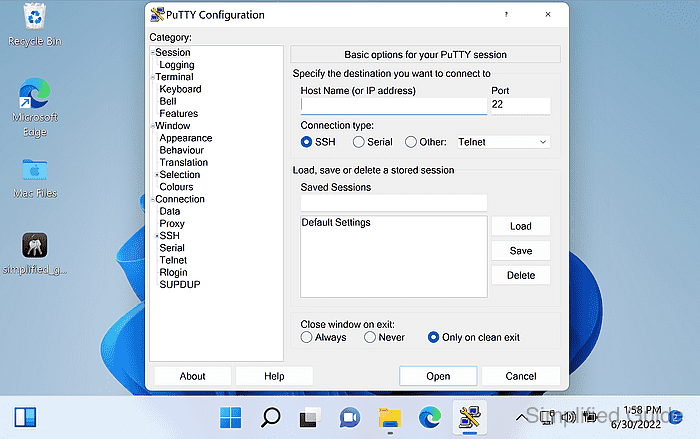
- Enter the server Host Name or IP address and Port.
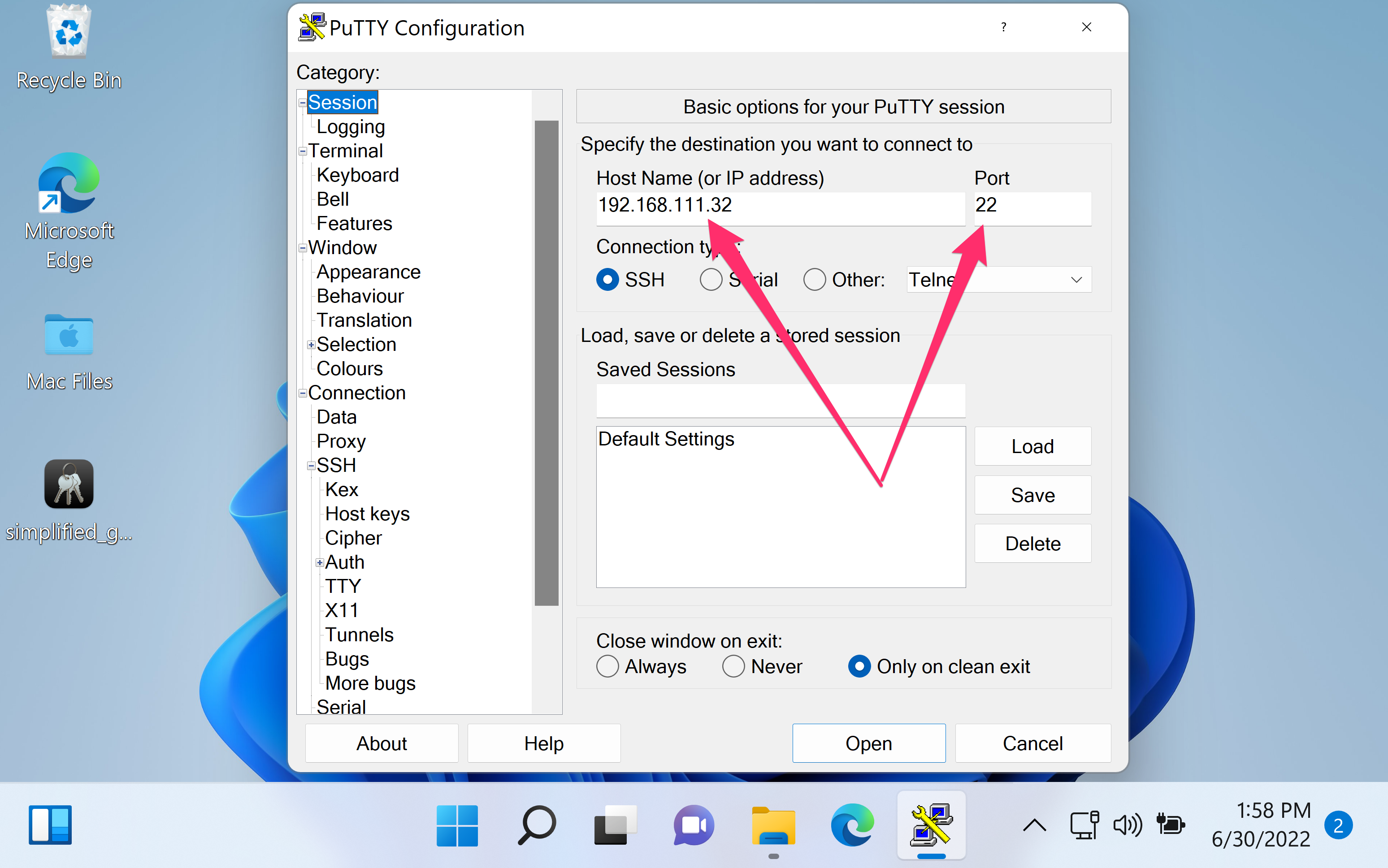
- Navigate to Connection → SSH → Auth from the sidebar menu.
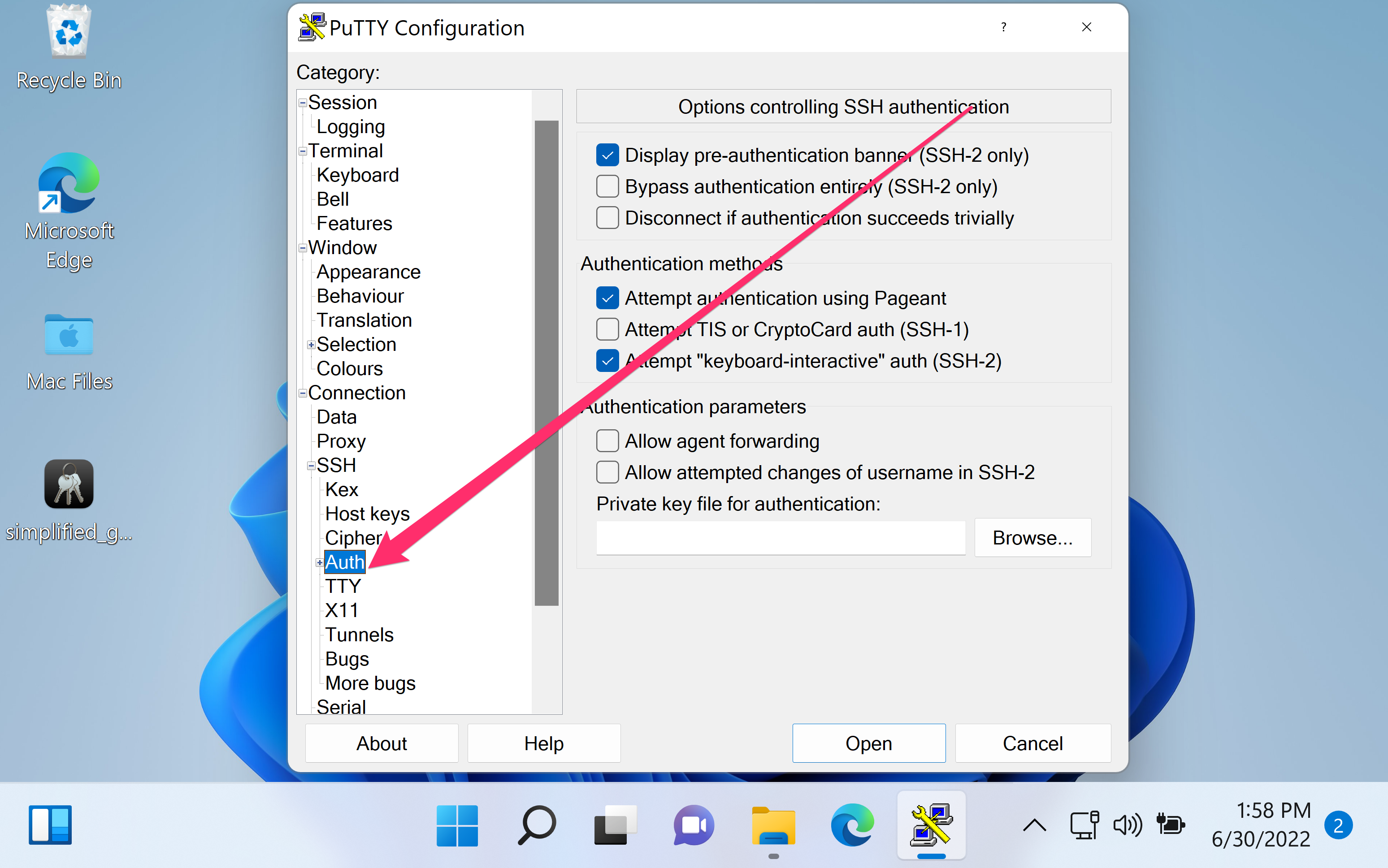
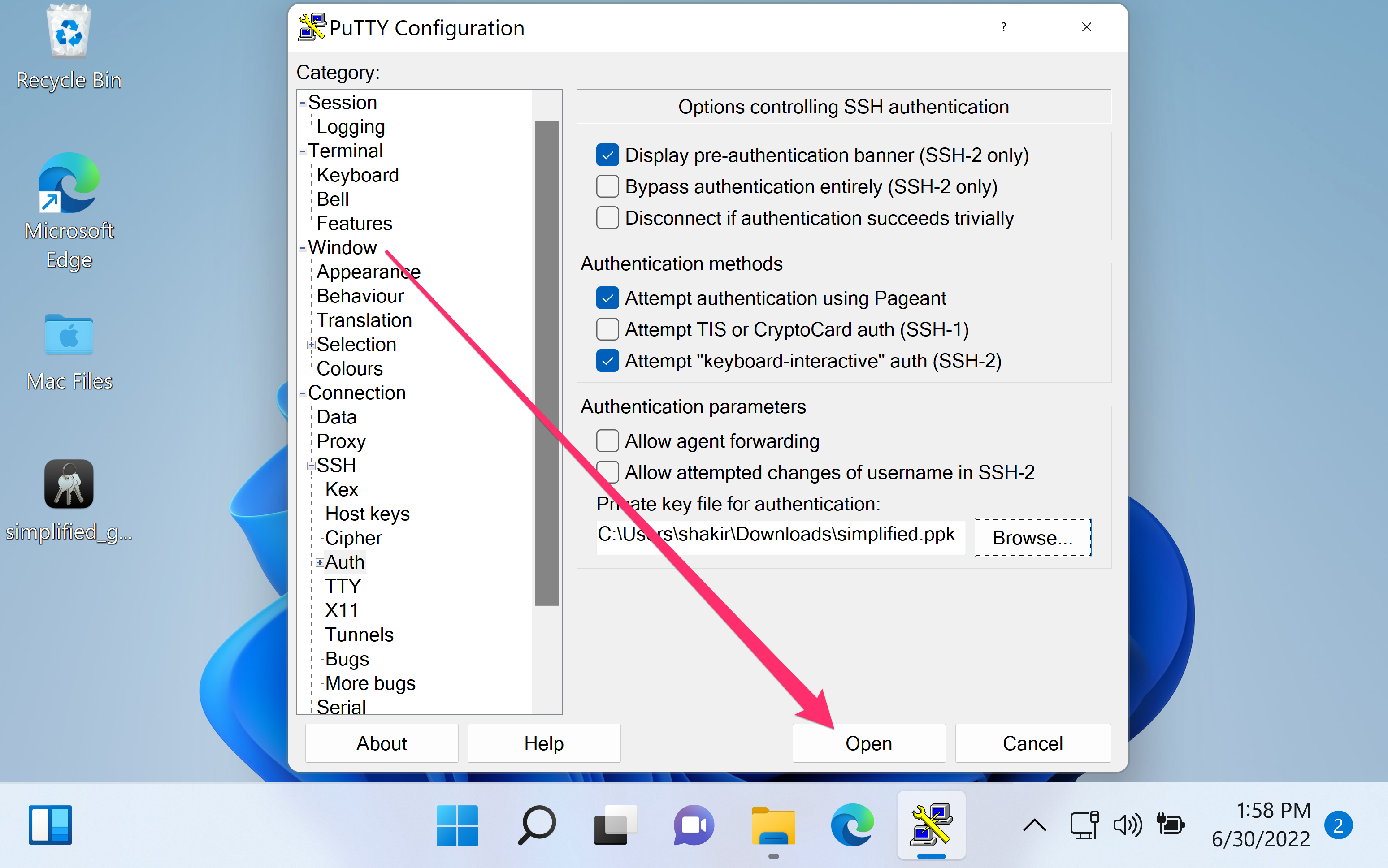
- Click Browse next to Private key file for authentication.
Saving the session profile under Session keeps the selected key for future connections.
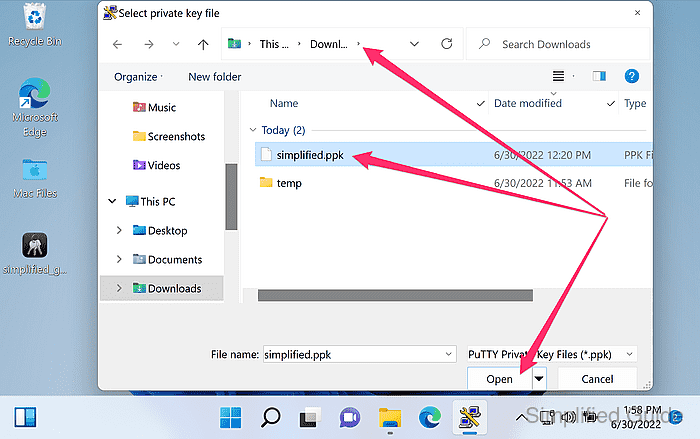
- Select the .ppk private key file and click Open.
- Start the SSH session by clicking Open in the main PuTTY window.
- Confirm the server host key prompt by clicking Yes after verifying the fingerprint.
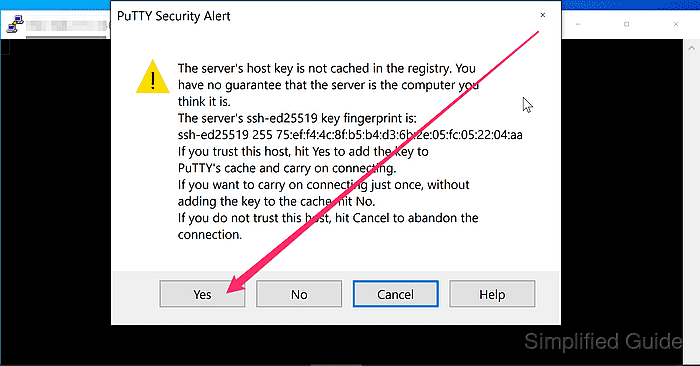
Accepting an unverified fingerprint can connect to an impostor host and expose credentials.
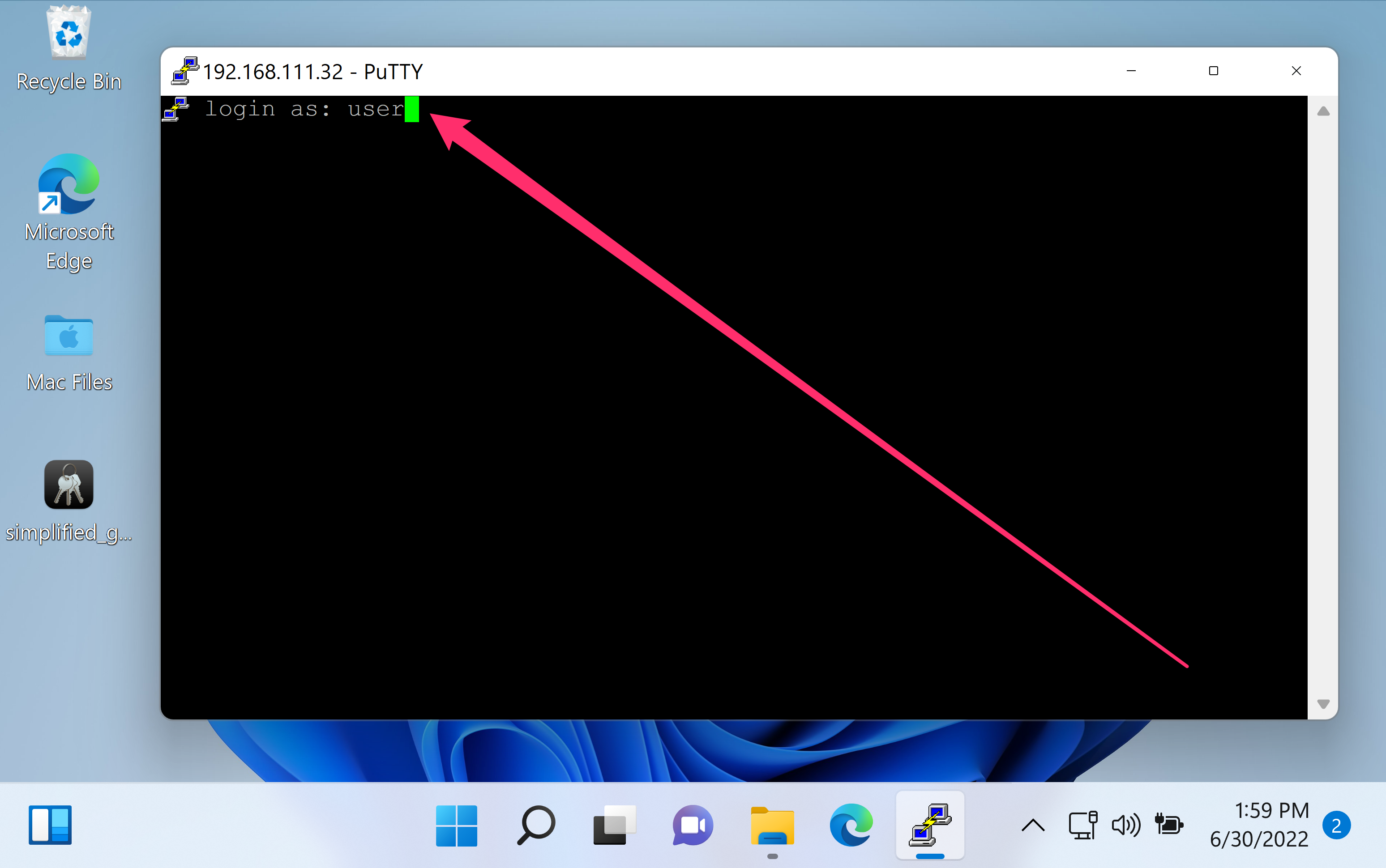
- Enter the SSH username and press Enter.
Set Auto-login username under Connection → Data to avoid retyping it.
- Enter the private key passphrase if prompted.
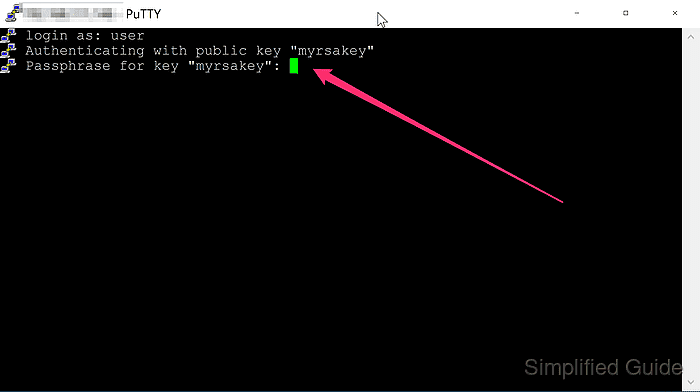
A passphrase protects the private key file if it is copied or stolen.
- Verify the session opens without a password prompt.

A password prompt usually means the key is not installed for that user or public key authentication is disabled on the server.

Mohd Shakir Zakaria is a cloud architect with deep roots in software development and open-source advocacy. Certified in AWS, Red Hat, VMware, ITIL, and Linux, he specializes in designing and managing robust cloud and on-premises infrastructures.
