SSH key pairs provide strong, passwordless authentication for remote access and automation. A private key remains on the local system while the matching public key is copied to each remote host, enabling encrypted logins and command execution without sending passwords over the network.
On most Linux systems, the OpenSSH client suite includes the ssh-keygen utility for creating key material. The tool generates a private key file along with a corresponding public key, typically stored under /home/<user>/.ssh, and supports multiple algorithms such as rsa, ecdsa and ed25519 with configurable key sizes.
Key choice and handling have direct security impact. Protecting the private key with a passphrase, enforcing strict file permissions, and keeping reliable backups reduce the risk of compromise or lockout. The following steps assume a terminal on a Linux system where ssh-keygen from OpenSSH is already installed and available in the shell path.
Steps to create public and private SSH key pairs using ssh-keygen:
- Launch a preferred terminal application.
- Run ssh-keygen without providing any options.
$ ssh-keygen Generating public/private ed25519 key pair.
ssh-keygen generates an ed25519 key pair when called with no options in modern OpenSSH builds. The key size and type can be changed using -b and -t options as in the example below.
$ ssh-keygen -b 521 -t ecdsa
Common key types include rsa, ecdsa and ed25519, with ed25519 recommended for most new deployments.
- Enter the location and filename to save the key pair.
Enter file in which to save the key (/home/user/.ssh/id_ed25519):
The default location is the .ssh directory in the user home folder and the default filename is id_<key_type>, for example /home/user/.ssh/id_ed25519.
- Enter a passphrase to secure the key (optional).
Enter passphrase (empty for no passphrase): Enter same passphrase again:
Omit the passphrase if the key is intended for fully automated passwordless SSH logins and cron jobs. For interactive use or sensitive access, a strong passphrase is recommended.
Related: How to set up passwordless SSH authentication - Confirm creation of the public and private SSH key pair in the chosen location.
Your identification has been saved in /home/user/.ssh/id_ed25519. Your public key has been saved in /home/user/.ssh/id_ed25519.pub.
The public key file uses the same base name as the private key with a .pub extension, for example /home/user/.ssh/id_ed25519.pub.
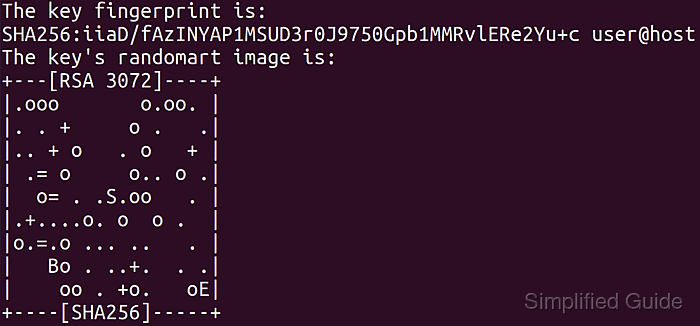
- Review the fingerprint and randomart for the newly created key.
The key fingerprint is: SHA256:Tb+G7DJR1HYf+QaGTwJu4gjnqAiV6AoNsoIPeIXfkNs user@host The key's randomart image is: +--[ED25519 256]--+ | .o . .| | . o . .. = =o | |+ + = . ..+. * oo| |== o X o =.. . +| |O.o + E S.. . . | |== . .. . . | |o o .o o | | o. . | | o. | +----[SHA256]-----+
The key fingerprint provides a short, unique identifier that can be compared when installing the public key on remote systems.
- Verify permissions of the created key files (optional).
$ ls -l ~/.ssh/id_ed25519* -rw------- 1 user user 399 Jan 10 12:19 /home/user/.ssh/id_ed25519 -rw-r--r-- 1 user user 91 Jan 10 12:19 /home/user/.ssh/id_ed25519.pub
The private key file (/home/user/.ssh/id_ed25519) uses strict permissions where only the owner has read and write access; group and other users have no permissions. The public key is world-readable.
Related: How to resolve the "SSH Unprotected Private Key File" warning in SSH

Mohd Shakir Zakaria is a cloud architect with deep roots in software development and open-source advocacy. Certified in AWS, Red Hat, VMware, ITIL, and Linux, he specializes in designing and managing robust cloud and on-premises infrastructures.
