Private-key authentication in SSH depends on keeping the private key readable only by its owner, so any other access is treated as a security risk and blocks key-based login. An “UNPROTECTED PRIVATE KEY FILE” warning appears when the permissions on the private key are too permissive, causing OpenSSH to ignore the key and fall back to other authentication methods such as passwords.
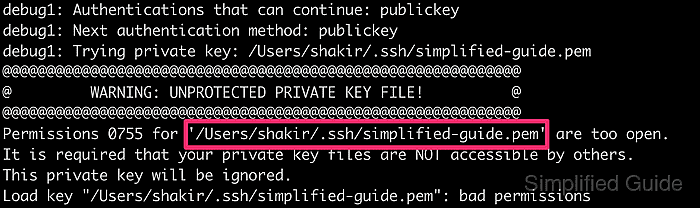
During authentication, OpenSSH validates the permissions and ownership of each private key before attempting to use it. When the unprotected key banner appears together with permissions like 0755 or 0644, the key is considered usable by other accounts and is rejected. A typical failure looks similar to the following excerpt.
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ @ WARNING: UNPROTECTED PRIVATE KEY FILE! @ @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ Permissions 0755 for '/home/user/.ssh/unprotected.pem' are too open. It is required that your private key files are NOT accessible by others. This private key will be ignored. Load key "/home/user/.ssh/unprotected.pem": bad permissions user@host.example.net: Permission denied (publickey,password).
Overly permissive keys are often created when copying files from another system, downloading keys from a browser, or unpacking archives that do not preserve secure permissions. Misconfigured umask values or shared directories can have the same effect, leaving the private key readable by other users and increasing the risk of key theft. Restricting the file mode to owner-only access restores secure key use and removes the warning; the steps below focus on Linux, but the same permissions are also required on macOS and other OpenSSH platforms.
Steps to change SSH private key permission in Linux:
- Locate the private SSH key file on the system, usually under ~/.ssh with a .pem or .key extension.
- Open a terminal window with access to the account that owns the private key.
- Verify the current permissions and ownership of the private key file (optional).
$ ls -l ~/.ssh/unprotected.pem -rwxr-xr-x 1 user user 399 Jan 10 12:25 /home/user/.ssh/unprotected.pem
Permissions such as -rwxr-xr-x or -rw-r--r-- indicate that the group or other users can read the key and will trigger the warning.
- Change the private key permissions to owner read and write only so that group and other users lose all access.
$ chmod 600 ~/.ssh/unprotected.pem
The file must be owned by the correct user with mode 600, giving that user read and write access while denying all permissions to the group and others.
- Confirm that the new mode is restricted to the owner and that no execute bits remain set.
$ ls -l ~/.ssh/unprotected.pem -rw------- 1 user user 399 Jan 10 12:25 /home/user/.ssh/unprotected.pem
- Attempt to connect to the server again using the fixed private key.
$ ssh -i ~/.ssh/unprotected.pem user@host.example.net 'hostname' host
The absence of the “UNPROTECTED PRIVATE KEY FILE” banner and a successful login indicate that the permissions are now acceptable to OpenSSH.

Mohd Shakir Zakaria is a cloud architect with deep roots in software development and open-source advocacy. Certified in AWS, Red Hat, VMware, ITIL, and Linux, he specializes in designing and managing robust cloud and on-premises infrastructures.
