In Linux, file and folder permissions control who can read, modify, or execute data on a system and form a core part of basic security hardening. Correctly scoped permissions reduce the risk of accidental data loss and limit what untrusted users or services can do in shared environments.
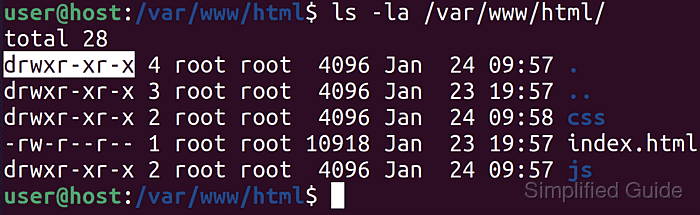
Each filesystem object is associated with three permission sets: one for the owner (user), one for the group, and one for all other users. Long listings such as drwxr-xr-x indicate whether the object is a directory or regular file and show read (r), write (w), and execute (x) bits for user, group, and others, while a dash (-) indicates that a particular permission is not granted. Commands such as chmod adjust these bits using symbolic forms like u=rwx,g=rx,o= when tuning access for different roles.
The same permissions can be expressed in octal notation such as 755 or 640, where each digit encodes the read, write, and execute bits for user, group, and others in binary. The tables below map symbolic, binary, and octal representations and act as a quick reference when choosing secure defaults. Advanced mechanisms such as ACL, SELinux, and AppArmor add more granular or mandatory access controls but remain outside the scope here, keeping the focus on standard ownership and mode changes with chmod.
| Category | Letter | Permission | Octal | Read | Write | Execute |
|---|---|---|---|---|---|---|
| User (owner) | u | rwx | 7 | Yes | Yes | Yes |
| Group | g | r-x | 5 | Yes | No | Yes |
| Others | o | r-x | 5 | Yes | No | Yes |
| Octal | Binary | Permission |
|---|---|---|
| 0 | 000 | none |
| 1 | 001 | execute |
| 2 | 010 | write |
| 3 | 011 | write, execute |
| 4 | 100 | read |
| 5 | 101 | read, execute |
| 6 | 110 | read, write |
| 7 | 111 | read, write, execute |
Steps to set file and folder permission on Linux:
- Check the current permissions of a file or folder in both octal and symbolic form.
$ stat -c "%a : %A" /root/sg-work/perm-demo/alpha.txt 644 : -rw-r--r--
The first value is the octal mode, and the second is the symbolic representation shown in ls -l output.
- Add write permission for the group using symbolic mode.
$ sudo chmod g+w /root/sg-work/perm-demo/alpha.txt
The g+w expression adds write permission for the group while leaving all other bits unchanged.
- Remove read permission for others to prevent world-readable access.
$ sudo chmod o-r /root/sg-work/perm-demo/alpha.txt
Removing read access for others helps keep sensitive content from being exposed to all local users.
- Set read and execute permissions for the owner (user) explicitly, replacing any existing owner bits.
$ sudo chmod u=rx /root/sg-work/perm-demo/alpha.txt
The u=rx form overwrites the owner’s permissions with read and execute, dropping any previous write bit.
- Verify the updated permissions of the file.
$ stat -c "%a : %A" /root/sg-work/perm-demo/alpha.txt 560 : -r-xrw----
The mode 560 corresponds to user r-x, group rw-, and no permissions for others.
- Set the same permissions using octal notation for all entries directly in a directory.
$ sudo chmod 560 /root/sg-work/perm-demo/*
Without --recursive (-R), permissions apply only to items directly inside the directory, not to nested subdirectories and their contents.
- Apply the permissions recursively to all files and folders under a directory.
$ sudo chmod -R 560 /root/sg-work/perm-demo
Recursive permission changes can break services or access if run on the wrong path or with an incorrect mode; confirm both before executing.
- Check the current permissions for all files and folders in the directory tree.
$ sudo ls -l /root/sg-work/perm-demo total 8 -r-xrw---- 1 root root 6 Jan 10 12:15 alpha.txt -r-xrw---- 1 root root 5 Jan 10 12:15 beta.txt
Entries starting with d are directories; verify that user, group, and others bits match the expected access pattern for the application.

Mohd Shakir Zakaria is a cloud architect with deep roots in software development and open-source advocacy. Certified in AWS, Red Hat, VMware, ITIL, and Linux, he specializes in designing and managing robust cloud and on-premises infrastructures.
