Slow SSH authentication delays remote access and interrupts workflows, especially when connections to remote systems are opened many times per day. Reducing the time between running an ssh command and receiving a shell prompt makes interactive administration and automation far more responsive.
During connection setup, the client and server negotiate keys and ciphers, perform host key checks, may run reverse DNS queries, and probe multiple authentication mechanisms such as GSSAPI, public keys, and passwords. Each extra lookup, round-trip, and unused authentication method adds latency, so trimming unnecessary work from this exchange directly improves perceived speed.
Tuning focuses on adjusting sshd and ssh configuration, selecting efficient ciphers, enabling connection sharing, and preferring key-based authentication on Linux systems. Changes to /etc/ssh/sshd_config and client files such as /etc/ssh/ssh_config or /~/.ssh/config must be applied carefully because invalid directives can block new logins or weaken security if unsafe algorithms are enabled.
Steps to improve SSH performance:
- Measure the current SSH login time as a baseline.
$ time ssh -i ~/.ssh/id_ed25519 -o PubkeyAuthentication=yes -o PreferredAuthentications=publickey user@host.example.net 'exit' real 0m0.121s user 0m0.021s sys 0m0.005s
Replace user@host.example.net with the real login and host, and record the real time value for comparison after tuning.
- Open /etc/ssh/sshd_config in a text editor on the SSH server.
$ sudo nano /etc/ssh/sshd_config
Syntax errors in /etc/ssh/sshd_config can prevent new SSH sessions until corrected, so keep an existing root session or console available while editing.
- Disable reverse DNS lookups by setting UseDNS to no in the server configuration.
# Example lines in /etc/ssh/sshd_config #UseDNS yes UseDNS no
Reverse DNS lookups cause the server to query name servers for each client connection and can add several seconds of delay when DNS is slow or misconfigured.
- Disable GSSAPI authentication if the environment does not require Kerberos or similar mechanisms.
# Example lines in /etc/ssh/sshd_config #GSSAPIAuthentication yes GSSAPIAuthentication no
Turning off GSSAPIAuthentication skips Kerberos negotiation when only public key or password authentication is used, reducing round-trips during login.
- Validate the updated sshd configuration syntax before applying changes.
$ sudo sshd -t
Absence of output indicates that the configuration parses correctly and is safe to reload.
- Restart the ssh service to apply the server-side configuration changes.
$ sudo systemctl restart ssh
If the service fails to start because of configuration problems, new SSH connections will be refused until the issue is fixed.
- Enable multiplexing in the client configuration to reuse existing connections.
$ mkdir -p ~/.ssh/muxmasters $ cat >> ~/.ssh/config <<'EOF' Host host-fast HostName host.example.net User user IdentityFile ~/.ssh/id_ed25519 ControlMaster auto ControlPath ~/.ssh/muxmasters/%C ControlPersist 10m EOF
multiplexing keeps one master connection open so additional sessions to the same host start almost instantly during the ControlPersist period.
Related: How to use multiplexing in SSH
- Restrict the client to preferred authentication methods to avoid slow, unused options.
$ ssh -o PreferredAuthentications=publickey -o PubkeyAuthentication=yes host-fast
Limiting PreferredAuthentications prevents the client from trying slower mechanisms such as keyboard-interactive or GSSAPI when they are not needed.
- Use key-based passwordless authentication so repeated logins do not require typing a password.
$ ssh-copy-id -i ~/.ssh/id_ed25519.pub user@host.example.net Number of key(s) added: 1 Now try logging into the machine, with: "ssh -i ~/.ssh/id_ed25519 user@host.example.net" and check to make sure that only the key(s) you wanted were added.
Protect private keys with a passphrase so that passwordless logins do not weaken account security.
- Prefer faster modern ciphers on the client to reduce CPU overhead during session setup.
$ cat >> ~/.ssh/config <<'EOF' Host host-fast Ciphers chacha20-poly1305@openssh.com,aes128-gcm@openssh.com EOF
chacha20-poly1305@openssh.com is designed for high performance on systems without hardware AES acceleration while remaining secure.
Related: How to change SSH ciphers
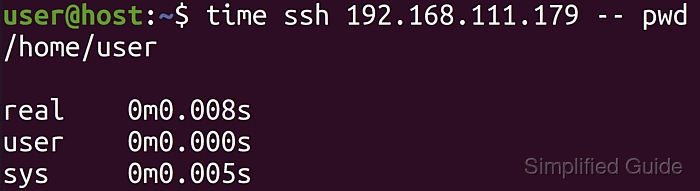
- Compare the optimized SSH login time with the initial baseline.
$ time ssh host-fast 'exit' real 0m0.008s user 0m0.002s sys 0m0.002s
A lower real time indicates that reusing connections and tuning authentication settings has reduced login latency.

Mohd Shakir Zakaria is a cloud architect with deep roots in software development and open-source advocacy. Certified in AWS, Red Hat, VMware, ITIL, and Linux, he specializes in designing and managing robust cloud and on-premises infrastructures.
