Controlling the order of SSH authentication methods improves login speed and enforces consistent security policies. Prioritizing publickey over password, for example, reduces exposure to brute-force attacks and keeps automated access predictable.
The PreferredAuthentications option in the OpenSSH client defines which methods are attempted and in what sequence. Values are usually configured in /etc/ssh/ssh_config for system-wide defaults or in ~/.ssh/config for per-user overrides, and can also be specified on the command line with ssh -o options. Verbose output from ssh reveals which methods are offered by the server and which one the client selects.
Choosing an inappropriate order or disabling supported methods can prevent successful logins. Restricting authentication to publickey only, for example, blocks access from users without keys even if password authentication remains enabled on the server. Configuration changes should always be tested with verbose logging while a fallback access path remains available.
Related: How to improve SSH performance and speed
Related: How to allow or disallow SSH password authentication
PreferredAuthentications
Specifies the order in which the client should try authentication methods.
This enables prioritizing one method (for example, keyboard-interactive) over another (for example, password).
The default in many OpenSSH clients is:
gssapi-with-mic,hostbased,publickey,keyboard-interactive,password
Steps to set the preferred authentication method for SSH:
- Open a terminal on the client system.
- Display the effective PreferredAuthentications value for a specific host.
$ ssh -G host.example.net | grep -i preferredauthentications preferredauthentications publickey,password
The ssh -G option prints the fully expanded configuration that applies to a host after processing all ssh_config files and matching Host blocks.
- Read the ssh_config manual section describing PreferredAuthentications.
$ man ssh_config ##### snipped ##### PreferredAuthentications Specifies the order in which the client should try authentication methods. This allows a client to prefer one method (e.g. keyboard-interactive) over another method (e.g. password). The default is: gssapi-with-mic,hostbased,publickey, keyboard-interactive,password ##### snipped ##### - Test a one-off connection with an explicit PreferredAuthentications list.
$ ssh -o PreferredAuthentications=publickey backupuser@host.example.net backupuser@host.example.net: Permission denied (publickey,password).

Specifying only methods that the server does not accept, or omitting password where no key exists, prevents login until the option or configuration is corrected.
- Open the per-user SSH client configuration file in a text editor.
$ vi ~/.ssh/config
Use /etc/ssh/ssh_config for system-wide defaults when elevated privileges are available; user configuration in ~/.ssh/config always overrides matching settings from the global file.
- Add or update a Host block with the desired PreferredAuthentications order and save the file.
Host * PreferredAuthentications publickey,passwordThe example restricts the client to attempt only publickey first and password as a fallback for all hosts; define more specific Host patterns above this block for per-host preferences.
- Connect to the host with verbose logging to confirm the new authentication order.
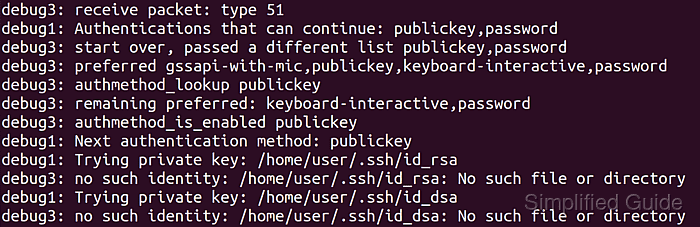
$ ssh -vv host.example.net ##### snipped ##### debug1: Authentications that can continue: publickey,password debug1: Next authentication method: publickey ##### snipped #####

Verbose output confirms that ssh now prefers publickey and only falls back to password if key-based authentication fails or no usable key is present.
- Confirm that the reported methods in verbose output match the configured PreferredAuthentications list and adjust the configuration if the sequence differs from the intended policy.

Mohd Shakir Zakaria is a cloud architect with deep roots in software development and open-source advocacy. Certified in AWS, Red Hat, VMware, ITIL, and Linux, he specializes in designing and managing robust cloud and on-premises infrastructures.
