Failed SSH login attempts are a primary signal of brute-force attacks, credential stuffing, and opportunistic scanning against Internet-facing systems. Monitoring these events highlights suspicious sources, reveals weak accounts that attract guessing, and provides evidence when intrusion attempts escalate into incidents.
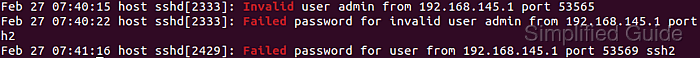
On Linux systems, OpenSSH logs authentication activity through the system logging stack, either in the persistent systemd journal or in classic text log files under /var/log. Entries typically include timestamp, hostname, sshd process ID, message type, username, and remote IP address, which makes it possible to filter out failed attempts by message text and aggregate them by source.
Access to authentication logs usually requires elevated privileges and differs between distributions because of distinct logging facilities and file paths. Journal retention, log rotation, and any remote log forwarding also influence how much history remains available. Knowing whether the system uses /var/log/auth.log, /var/log/secure, or only the journal is essential before extracting statistics on failed login attempts.
Steps to check failed SSH login attempts:
- Open a terminal with sudo privileges.
$ whoami user
- Review the systemd journal for SSH messages containing failure patterns.
$ sudo journalctl _SYSTEMD_UNIT=ssh.service | egrep -i "fail|invalid|did" Dec 29 03:41:53 host sshd[3772]: Invalid user deploy from 203.0.113.10 port 56906 Dec 29 03:41:55 host sshd[3772]: Failed password for invalid user deploy from 203.0.113.10 port 56906 ssh2 Dec 29 03:41:57 host sshd[3780]: Invalid user operator from 203.0.113.10 port 56914 Dec 29 03:41:59 host sshd[3780]: Failed password for invalid user operator from 203.0.113.10 port 56914 ssh2 Dec 29 03:42:03 host sshd[3784]: Failed password for user from 203.0.113.10 port 47308 ssh2 ##### snipped #####
Filtering directly in the journal is useful on systems that do not write /var/log/auth.log or /var/log/secure.
- Determine the logging facility type used by the SSH server.
$ sudo sshd -T | grep syslogfacility syslogfacility AUTH
Distribution Logging facility Ubuntu AUTH Red Hat AUTHPRIV - Locate the log file corresponding to the configured logging facility.
$ sudo grep -nir auth /etc/[r]syslog* /etc/rsyslog.d/50-default.conf:8:auth,authpriv.* /var/log/auth.log /etc/rsyslog.d/50-default.conf:9:*.*;auth,authpriv.none -/var/log/syslog /etc/rsyslog.d/50-default.conf:29:# auth,authpriv.none;\ /etc/rsyslog.d/50-default.conf:32:# auth,authpriv.none;\
Distribution SSH log file Ubuntu /var/log/auth.log Red Hat /var/log/secure Generic /var/log/messages, /var/log/syslog - Extract entries for failed SSH login attempts from the authentication log file.
$ sudo grep -E "sshd.*(Failed|Invalid|Did)" /var/log/auth.log | grep -v COMMAND 2025-12-29T03:41:53.308674+00:00 host sshd[3772]: Invalid user deploy from 203.0.113.10 port 56906 2025-12-29T03:41:55.006533+00:00 host sshd[3772]: Failed password for invalid user deploy from 203.0.113.10 port 56906 ssh2 2025-12-29T03:41:57.130579+00:00 host sshd[3776]: Failed password for backup from 203.0.113.10 port 56908 ssh2 2025-12-29T03:41:57.475779+00:00 host sshd[3780]: Invalid user operator from 203.0.113.10 port 56914 2025-12-29T03:41:59.389225+00:00 host sshd[3780]: Failed password for invalid user operator from 203.0.113.10 port 56914 ssh2 ##### snipped #####
Searched keywords Reason Failed password for … Incorrect password used to log in Invalid user … Unknown user used to log in Did not receive identification … (optional) Login not actually attempted, often caused by port scanners - Retrieve the list of remote IP addresses associated with failed SSH login entries.
$ sudo grep -E "sshd.*(Failed|Invalid|Did)" /var/log/auth.log | grep -v COMMAND | awk -F 'from ' '{ print $2 }' | awk '{ print $1 }' 203.0.113.10 203.0.113.10 203.0.113.10 203.0.113.10 ##### snipped ##### - Identify unique IP addresses that generated failed login attempts.
$ sudo grep -E "sshd.*(Failed|Invalid|Did)" /var/log/auth.log | grep -v COMMAND | awk -F 'from ' '{ print $2 }' | awk '{ print $1 }' | sort | uniq 203.0.113.10 - Count the number of failed SSH login attempts originating from each IP address.
$ sudo grep -E "sshd.*(Failed|Invalid|Did)" /var/log/auth.log | grep -v COMMAND | awk -F 'from ' '{ print $2 }' | awk '{ print $1 }' | sort | uniq -c 12 203.0.113.10Sorting and counting by IP address highlights sources responsible for repeated failures and can feed into blocking rules or intrusion detection policies.

Mohd Shakir Zakaria is a cloud architect with deep roots in software development and open-source advocacy. Certified in AWS, Red Hat, VMware, ITIL, and Linux, he specializes in designing and managing robust cloud and on-premises infrastructures.
