Forcibly logging out a user on Linux maintains control over shared systems when sessions hang, permissions change, or access must be revoked immediately. Removing only the problematic login preserves availability for other users and avoids the disruption of stopping services or rebooting.
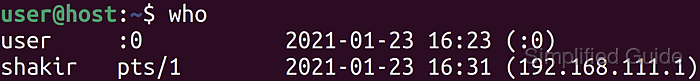
Utilities such as who, ps, and pkill correlate login names with active sessions and the processes backing them. Locating the interactive shell or session leader by process ID makes it possible to terminate a single login cleanly instead of disconnecting networking or restarting the host.
Forcible termination discards unsaved work and can interrupt database clients, editors, or file transfers mid-operation, so it suits only cases where a normal logout is impossible or unsafe. Commands that target all processes for an account affect every terminal and background job owned by that user, which is especially sensitive for shared accounts and production services on multi-user servers.
Steps to force user logout in Linux:
- Open a terminal on the Linux system with sudo-capable credentials.
$ whoami user
- List currently logged-in users to identify the account and session to remove.
$ who audituser pts/0 2026-01-10 12:15 (203.0.113.10) user pts/1 2026-01-10 12:15 (203.0.113.10)
The second column, such as pts/1, indicates the terminal attached to the login session.
- Record the target username and its terminal identifier for later reference.
Matching the username and pts value helps distinguish multiple logins for the same account.
- List processes owned by the target account to locate the interactive shell or session leader.
$ ps -u audituser PID TTY TIME CMD ##### snipped ##### 3853 ? 00:00:00 sshd 3854 pts/0 00:00:00 sleep
- Terminate the shell process for the chosen session to close that specific login.
$ sudo kill 3854
sleep is the interactive placeholder process in this example; stopping it cleanly ends the user’s terminal session.
- Optionally end all processes for the account when every session for that user must be disconnected.
$ sudo pkill -u audituser
Stopping all processes for an account also terminates background jobs and service-like tasks owned by that user, which can interrupt running workloads.
- Forcefully kill any remaining processes for the account that ignore normal termination signals.
$ sudo pkill -9 -u audituser
Using SIGKILL bypasses cleanup and can leave temporary files or partially written data on disk.
- Verify that the account is no longer listed as logged in.
$ who user pts/0 2026-01-10 12:15 (203.0.113.10)
Absence of the username in the who output confirms that all interactive sessions for that account have been closed.

Mohd Shakir Zakaria is a cloud architect with deep roots in software development and open-source advocacy. Certified in AWS, Red Hat, VMware, ITIL, and Linux, he specializes in designing and managing robust cloud and on-premises infrastructures.
