Cookies provide stateful context for HTTP clients, allowing servers to associate individual requests with a specific session or preference set. When scripted with cURL, cookies reproduce browser-like behavior so automated calls can interact with authenticated pages, region-specific content, or feature flags in a predictable way.
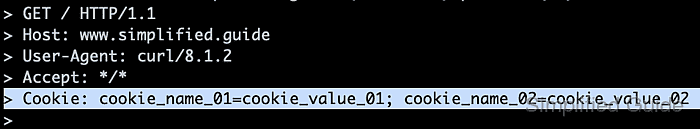
Under the hood, cookies travel in the Cookie request header and are refreshed by servers through Set-Cookie response headers. cURL attaches cookies with the --cookie option, either from a literal name-value string or from a file in the classic Netscape cookie format, and can persist refreshed values using a dedicated cookie-jar file.
Careless handling of cookie values can leak session identifiers, expose personal data, or violate domain and path scoping rules. Cookie files belong on trusted storage only, should not be checked into version control, and require attention to options such as Secure, HttpOnly, and SameSite when testing behavior across multiple environments.
Steps to use cookies in cURL requests:
- Run a baseline cURL request without cookies to inspect the default response.
$ curl --silent https://httpbin.org/cookies { "cookies": {} }
The https://httpbin.org/cookies endpoint returns a JSON object showing which cookies the server received from the client.
- Send a request with a single cookie using --cookie to confirm that the server receives it.
$ curl --silent --cookie "session=abc123" https://httpbin.org/cookies { "cookies": { "session": "abc123" } }
The --cookie “name=value” syntax attaches a single cookie as a Cookie header for that request.
- Attach multiple cookies in one header by separating pairs with semicolons inside --cookie.
$ curl --silent --cookie "session=abc123; theme=dark; lang=en" https://httpbin.org/cookies { "cookies": { "lang": "en", "session": "abc123", "theme": "dark" } }
Multiple cookies travel in a single Cookie header, with semicolons delimiting each name=value pair.
- Load cookies from a file in Netscape format by passing the file path to --cookie.
$ curl --silent --cookie "./curl-cookies.txt" https://httpbin.org/cookies { "cookies": { "session": "abc123" } }
Cookie files often contain long-lived session tokens; storing files such as /curl-cookies.txt on shared or unencrypted storage can allow account hijacking.
- Persist refreshed cookies back into the same file by combining --cookie with --cookie-jar.
$ curl --silent --cookie "./curl-cookies.txt" --cookie-jar "./curl-cookies.txt" https://httpbin.org/cookies/set/session/def456 { "cookies": { "session": "def456" } }
Using the same file for --cookie and --cookie-jar keeps the cookie store synchronized as the server updates session values.
- Inspect the cookie file contents with a text display utility to verify what is stored.
$ sed -n '1,6p' curl-cookies.txt # Netscape HTTP Cookie File # https://curl.se/docs/http-cookies.html # This file was generated by libcurl! Edit at your own risk. httpbin.org FALSE / FALSE 0 session def456
The Netscape cookie file format uses tab-separated fields for domain, path, security flags, expiry, name, and value, which cURL reads and updates automatically.
- Verify effective cookie usage by repeating the request and checking that the expected cookies appear in the response.
$ curl --silent --cookie "./curl-cookies.txt" https://httpbin.org/cookies { "cookies": { "session": "def456" } }
Successful cookie handling typically shows the intended names and values in the JSON output or in application-specific responses from authenticated or personalized endpoints.

Mohd Shakir Zakaria is a cloud architect with deep roots in software development and open-source advocacy. Certified in AWS, Red Hat, VMware, ITIL, and Linux, he specializes in designing and managing robust cloud and on-premises infrastructures.
Comment anonymously. Login not required.
