Manually creating a cookie file for cURL provides fine-grained control over session state during scripted HTTP requests. Instead of relying on a browser to manage cookies, a hand-crafted file can reproduce authentication, preferences, or tracking keys exactly when automation or testing needs them.
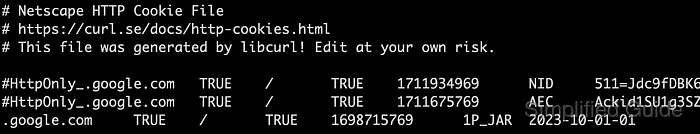
The Netscape HTTP cookie file format represents cookies as one line per entry with fixed columns for domain, tail-matching flag, path, secure flag, expiry time, name, and value. cURL reads this format when the --cookie option points at a file, translating each line into outgoing Cookie headers that match the request host and path.
Because cookie files store raw session tokens in plain text, incorrect permissions can expose accounts to other users on the same system. Misconfigured domains, paths, or expiry timestamps may silently prevent cookies from being sent, so careful formatting and verification against a test endpoint are essential before depending on the file in production.
Related: How to save cookies from a cURL request
Related: How to use cookies in cURL requests
Steps to create a cookie file for cURL:
- Open a new plain-text file in a terminal text editor to act as the cookie store.
$ nano manual-cookies.txt
Any plain-text editor such as nano, vim, or a graphical editor can create the cookie file as long as the content is saved without additional formatting.
- Insert comment lines at the top that declare the Netscape HTTP cookie file format and describe the expected columns.
# Netscape HTTP Cookie File # Domain Tailmatch Path Secure Expiry Name Value
The leading hash characters mark comments that are ignored by cURL but document the layout for future edits.
- Add a first cookie entry using the standard column order of domain, tailmatch flag, path, secure flag, UNIX expiry time, name, and value separated by whitespace.
.example.net TRUE / FALSE 1893456000 SessionID 1234567890abcdef
The domain starting with a dot applies to the whole site, TRUE in the second field enables tail-matching for subdomains, FALSE in the secure field allows use over HTTP, and the expiry time is a UNIX timestamp in seconds.
- Append additional lines for every extra cookie that should be sent, adjusting domains, paths, and flags as required.
.example.net TRUE / FALSE 1893456000 SessionID 1234567890abcdef .example.net TRUE /account TRUE 1893456000 UserID myid
Each non-comment line represents exactly one cookie and can target different application areas by changing the path or require encryption by setting the secure flag to TRUE.
- Save the file and close the editor so the cookie entries are written to disk.
A quick way to confirm the file contents is to reopen it in the editor or run cat manual-cookies.txt in the terminal.
- Restrict access to the cookie file so only the current user can read and write it.
$ chmod 600 manual-cookies.txt
Plain-text cookie files often contain active session identifiers, so world-readable permissions can allow other local users to hijack authenticated sessions.
- Send a test request with cURL using the cookie file to confirm that the expected cookies are attached.
$ curl --silent --cookie manual-cookies.txt https://api.example.net/cookies { "cookies": { "SessionID": "1234567890abcdef" } }
Success indicators include a non-error status code and echoed cookie values that match the name-value pairs defined in the manual cookie file.

Mohd Shakir Zakaria is a cloud architect with deep roots in software development and open-source advocacy. Certified in AWS, Red Hat, VMware, ITIL, and Linux, he specializes in designing and managing robust cloud and on-premises infrastructures.
