Enabling HTTP Strict Transport Security (HSTS) forces modern browsers to stick to HTTPS for a site, shutting down protocol-downgrade attacks and accidental plain-HTTP visits that can leak cookies or session tokens.
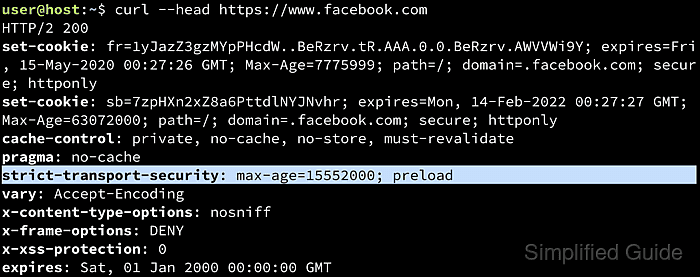
HSTS works by sending a Strict-Transport-Security response header over a successful HTTPS connection. The browser caches the policy for the declared max-age, automatically upgrading future HTTP navigations to HTTPS for that host while the policy is valid.
Because browsers ignore the header on HTTP responses, the HTTPS endpoint must be healthy first and plain HTTP should redirect to HTTPS. Examples below use the Debian-style Apache layout (/etc/apache2, apache2 service); adjust file paths and the service name on other distributions, and remember that rollback is client-cached (a temporary Strict-Transport-Security: max-age=0 over HTTPS is the usual way to clear a policy early).
Steps to enable HSTS in Apache:
- Confirm the site responds over HTTPS without certificate errors.
$ curl -sI https://host.example.net/ HTTP/1.1 200 OK Date: Sat, 10 Jan 2026 12:14:06 GMT Server: Apache/2.4.58 (Ubuntu) Last-Modified: Sat, 10 Jan 2026 05:32:07 GMT ETag: "29af-64801f6762249" Accept-Ranges: bytes Content-Length: 10671 Vary: Accept-Encoding Content-Type: text/html
- Confirm the HTTP endpoint redirects to HTTPS.
$ curl -sI http://host.example.net/ HTTP/1.1 301 Moved Permanently Date: Sat, 10 Jan 2026 12:14:06 GMT Server: Apache/2.4.58 (Ubuntu) Location: https://host.example.net/ Content-Type: text/html; charset=iso-8859-1
If the Location header does not point at https://host.example.net, add or fix the VirtualHost *:80 redirect before enabling HSTS.
- Enable the headers module to allow Apache to emit the Strict-Transport-Security header.
$ sudo a2enmod headers Enabling module headers. To activate the new configuration, you need to run: systemctl restart apache2
On RHEL-family systems, mod_headers is commonly available already and the service name is usually httpd.
- Open the site’s HTTPS VirtualHost configuration file.
$ sudo vi /etc/apache2/sites-available/host.example.net.conf
- Add the Strict-Transport-Security header inside the <VirtualHost *:443> block.
<VirtualHost *:443> # ... <IfModule mod_headers.c> Header always set Strict-Transport-Security "max-age=86400" </IfModule> </VirtualHost>A long max-age can lock browsers into HTTPS for that hostname until the timer expires, even if the header is later removed; start small, validate, then increase. Avoid includeSubDomains unless every subdomain is reachable over HTTPS, or browsers will refuse HTTP on subdomains too, and treat preload as a one-way door if a preload list submission is intended.
After a clean rollout, a common hardened value is max-age=31536000; includeSubDomains; a rollback policy is typically max-age=0 until clients expire the cached setting.
Related: Apache mod_headers documentation
- Validate the Apache configuration syntax.
$ sudo apache2ctl -t Syntax OK
- Restart the apache2 service to apply the change.
$ sudo systemctl restart apache2
A restart can briefly interrupt in-flight connections; use a reload if the deployment requires a graceful config apply.
- Check the HTTPS response headers for a Strict-Transport-Security line.
$ curl -sI https://host.example.net/ HTTP/1.1 200 OK Date: Sat, 10 Jan 2026 12:14:06 GMT Server: Apache/2.4.58 (Ubuntu) Strict-Transport-Security: max-age=86400 Last-Modified: Sat, 10 Jan 2026 05:32:07 GMT ETag: "29af-64801f6762249" Accept-Ranges: bytes Content-Length: 10671 Vary: Accept-Encoding Content-Type: text/html
HTTP/2 responses may show lower-case header names in curl output; the presence of the policy and the max-age value is what matters.

Mohd Shakir Zakaria is a cloud architect with deep roots in software development and open-source advocacy. Certified in AWS, Red Hat, VMware, ITIL, and Linux, he specializes in designing and managing robust cloud and on-premises infrastructures.
