Ignoring SSL certificate errors in wget is sometimes used when automation needs to download content from development, lab, or internal HTTPS servers that do not present a certificate trusted by public certificate authorities. Allowing transfers to continue despite validation failures keeps non-sensitive jobs running while infrastructure catches up with properly issued certificates.
$ wget https://selfsigned.example.com --2025-12-21 09:16:04-- https://selfsigned.example.com/ Resolving selfsigned.example.com (selfsigned.example.com)... 172.17.0.11 Connecting to selfsigned.example.com (selfsigned.example.com)|172.17.0.11|:443... connected. ERROR: cannot verify selfsigned.example.com's certificate, issued by 'C=US,O=Example Lab,CN=selfsigned.example.com': Self-signed certificate encountered. To connect to selfsigned.example.com insecurely, use `--no-check-certificate'.
During an HTTPS request, wget validates the server certificate chain against a local store of trusted certificate authorities and compares the certificate subject or subject alternative names with the requested hostname. If any part of this verification fails, wget aborts the transfer and prints a diagnostic error that often suggests adding the --no-check-certificate option or adjusting the configuration in ~/.wgetrc.
Bypassing verification removes an important security control, especially when traffic crosses untrusted networks or when credentials or sensitive data travel inside the same connection. Limiting the bypass to single commands, keeping changes in per-user configuration instead of system-wide files such as /etc/wgetrc, and reserving this behaviour for controlled environments reduces the risk of man-in-the-middle attacks.
Steps to bypass SSL certificate validation in Wget:
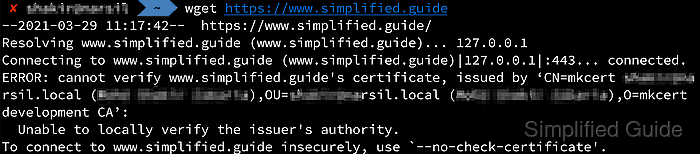
- Run wget against an HTTPS URL that currently produces a certificate error to confirm the failure state.
$ wget https://selfsigned.example.com --2025-12-21 09:16:04-- https://selfsigned.example.com/ Resolving selfsigned.example.com (selfsigned.example.com)... 172.17.0.11 Connecting to selfsigned.example.com (selfsigned.example.com)|172.17.0.11|:443... connected. ERROR: cannot verify selfsigned.example.com's certificate, issued by 'C=US,O=Example Lab,CN=selfsigned.example.com': Self-signed certificate encountered. To connect to selfsigned.example.com insecurely, use `--no-check-certificate'.
Diagnostic output confirms that certificate verification fails and that wget suggests the --no-check-certificate option.
- Repeat the download with the --no-check-certificate option to bypass SSL certificate validation only for this invocation.
$ wget --no-check-certificate https://selfsigned.example.com --2025-12-21 09:16:10-- https://selfsigned.example.com/ Resolving selfsigned.example.com (selfsigned.example.com)... 172.17.0.11 Connecting to selfsigned.example.com (selfsigned.example.com)|172.17.0.11|:443... connected. WARNING: cannot verify selfsigned.example.com's certificate, issued by 'C=US,O=Example Lab,CN=selfsigned.example.com': Self-signed certificate encountered. HTTP request sent, awaiting response... 200 OK Length: 578 [text/html] Saving to: 'index.html' 0K 100% 441M=0s 2025-12-21 09:16:10 (441 MB/s) - 'index.html' saved [578/578]Per-command use of --no-check-certificate keeps insecure behaviour limited to specific downloads instead of affecting every wget invocation.
- Add or update the per-user configuration file ~/.wgetrc to disable certificate checks persistently only for the current account, if that behaviour is acceptable for the environment.
$ printf 'check_certificate = off\n' >> ~/.wgetrc
Disabling certificate checks in configuration increases exposure to man-in-the-middle attacks and hostname spoofing, especially on untrusted networks.
On Windows the per-user configuration file is commonly read from %USERPROFILE%\.wgetrc.
- Run wget again on the same HTTPS URL without --no-check-certificate to confirm that the configuration change allows the transfer while still printing a warning.
$ wget https://selfsigned.example.com --2025-12-21 09:16:16-- https://selfsigned.example.com/ Resolving selfsigned.example.com (selfsigned.example.com)... 172.17.0.11 Connecting to selfsigned.example.com (selfsigned.example.com)|172.17.0.11|:443... connected. WARNING: cannot verify selfsigned.example.com's certificate, issued by 'C=US,O=Example Lab,CN=selfsigned.example.com': Self-signed certificate encountered. HTTP request sent, awaiting response... 200 OK Length: 578 [text/html] Saving to: 'index.html.1' 0K 100% 779M=0s 2025-12-21 09:16:16 (779 MB/s) - 'index.html.1' saved [578/578]Expected behaviour: the message changes from a fatal ERROR to a non-fatal WARNING while the content downloads successfully.
- List the downloaded files or inspect the most recent one to verify that the expected content was saved despite the certificate warnings.
$ ls -lh index.html* -rw-r--r-- 1 alex alex 578 Dec 21 07:26 index.html -rw-r--r-- 1 alex alex 578 Dec 21 07:26 index.html.1
Presence of the downloaded files with non-zero sizes confirms that wget completed the transfers while ignoring certificate errors.

Mohd Shakir Zakaria is a cloud architect with deep roots in software development and open-source advocacy. Certified in AWS, Red Hat, VMware, ITIL, and Linux, he specializes in designing and managing robust cloud and on-premises infrastructures.
Comment anonymously. Login not required.
