Checking syntax of SSH server configuration before applying changes prevents remote lockouts and downtime. The configuration file that controls sshd defines authentication rules, key handling, ciphers, login banners, and access restrictions, so a single typo can stop the daemon from starting when the service restarts. Configuration errors at this level may prevent remote logins and disrupt automation workflows.
The OpenSSH daemon reads directives from /etc/ssh/sshd_config when the service starts. In addition to runtime logs, sshd includes a dedicated test mode that parses the configuration, validates option names and values, and reports the exact line number of any problem without touching the running process. Combined with the init system's service management, syntax checks provide a safe way to confirm that updated settings are acceptable before reloading.
Because SSH often represents the only remote administration channel, every change to /etc/ssh/sshd_config carries some risk. Root or sudo privileges are required to edit the file, and restarting the service can terminate in-flight connections if configuration errors slip through. Maintaining a secondary access method, such as console access or an out-of-band management interface, reduces the impact of mistakes while configuration changes are validated.
Steps to check and validate sshd configuration:
- Open a terminal on the server with access to sudo privileges.
$ whoami user
- Open /etc/ssh/sshd_config in a text editor to view or change the SSH daemon configuration.
$ sudo vi /etc/ssh/sshd_config [sudo] password for user:
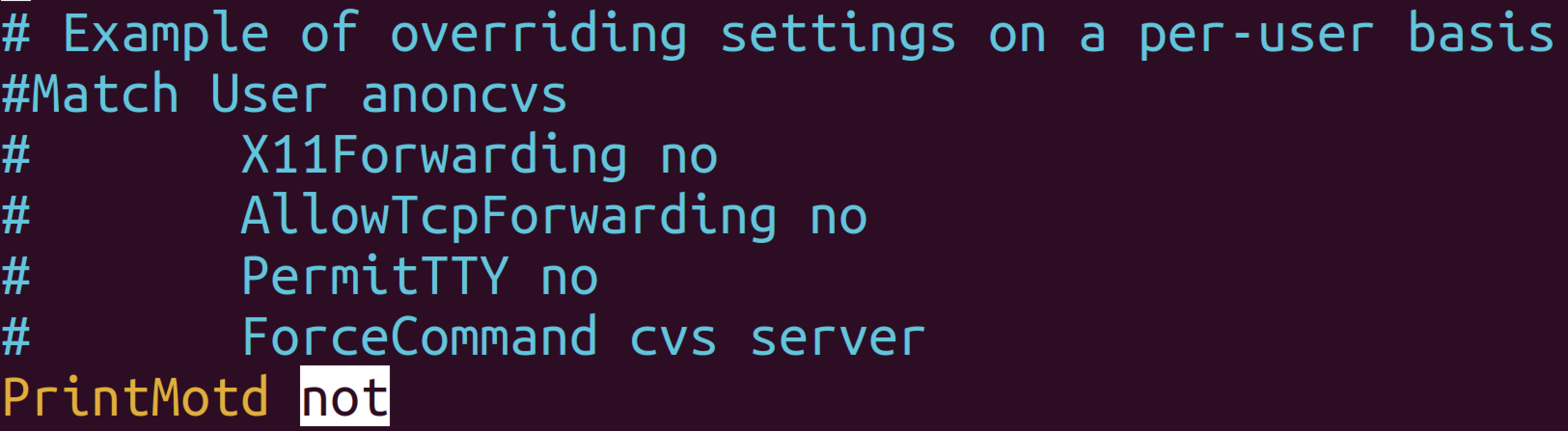
- Locate custom directives that may contain typos or unsupported options in the SSH configuration file.
# Example of overriding settings on a per-user basis #Match User anoncvs # X11Forwarding no # AllowTcpForwarding no # PermitTTY no # ForceCommand cvs server PrintMotd not
In this example, the directive PrintMotd not uses an invalid value and will cause a configuration error.
- Test the active SSH daemon configuration file using sshd in test mode.
$ sudo sshd -t /etc/ssh/sshd_config line 124: unsupported option "not".
-t Test mode. Only check the validity of the configuration file and sanity of the keys. This is useful for updating sshd reliably as configuration options may change.Use an alternate configuration path with sshd -t -f when validating a test file.
$ sudo sshd -t -f /etc/ssh/sshd_config_test
- Correct each reported error in /etc/ssh/sshd_config using the line numbers and option names shown in the test output.
- Run the test command again until it returns without any output.
$ sudo sshd -t $
No output from sshd indicates that the configuration file is syntactically valid.
- Restart the SSH service to load the validated configuration.
$ sudo systemctl restart ssh
Restarting the SSH service applies the new configuration and may terminate active sessions or prevent new logins if access control directives are misconfigured.
If the service unit on the system is named sshd instead of ssh, substitute sshd in the restart command.
- Verify that the SSH service is active after the restart.
$ sudo systemctl status ssh ● ssh.service - OpenBSD Secure Shell server Loaded: loaded (/lib/systemd/system/ssh.service; enabled; vendor preset: enabled) Active: active (running) since Mon 2025-05-13 10:15:01 UTC; 5s ago ##### snipped ##### - Confirm successful remote access by opening a new SSH connection from a separate client.
$ ssh user@server Welcome to Ubuntu 22.04.4 LTS ##### snipped #####

Mohd Shakir Zakaria is a cloud architect with deep roots in software development and open-source advocacy. Certified in AWS, Red Hat, VMware, ITIL, and Linux, he specializes in designing and managing robust cloud and on-premises infrastructures.
Comment anonymously. Login not required.
