Secure remote administration of servers often relies on encrypted SSH connections from a local Linux machine. Using SSH to reach a remote host enables command execution, file management, and troubleshooting without direct physical access to the hardware.
On Linux, the OpenSSH client provides the ssh command, which opens an encrypted session to a target host. During connection, the client verifies the server's host key, negotiates encryption parameters, and authenticates using either a password or SSH keys linked to an account on the remote system.
Reliable SSH access depends on network reachability, correct credentials, and suitable permissions on the remote system. Production environments usually favor SSH keys instead of passwords, and some servers listen on non-default ports or restrict logins to specific accounts, so connection details must match the server configuration.
Steps to SSH into server using OpenSSH client:
- Confirm that a valid user account exists on the target SSH server and is allowed to log in over SSH.
Ensure the account has a valid login shell and is permitted by any server-side AllowUsers or DenyUsers directives.
- Open a terminal on the local Linux system.
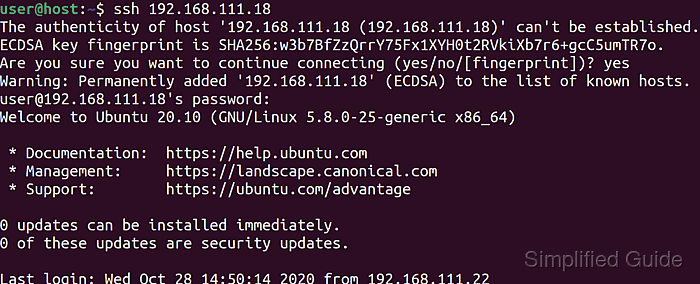
- Run the ssh command with the desired login name and host.
$ ssh user@host.example.net The authenticity of host 'host.example.net (203.0.113.50)' can't be established. ED25519 key fingerprint is SHA256:W8JdNBQbOLbfHYW4TeYr5i2x95TaTYG9MTc/q4FJZYc. This key is not known by any other names. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Accepting an unexpected host key fingerprint can expose credentials to a malicious server; verify the fingerprint through a trusted channel before proceeding.
- Approve the host key prompt only when the displayed fingerprint matches expectations.
Warning: Permanently added 'host.example.net' (ED25519) to the list of known hosts. user@host.example.net's password: ##### snipped #####
- Provide the account password when prompted or rely on configured SSH keys for key-based authentication.
For key-based logins, ensure the public key is present in /home/username/.ssh/authorized_keys and that directory and file permissions satisfy OpenSSH requirements.
- Verify the remote session by checking the shell prompt and running an identification command.
user@host:~$ id uid=1000(user) gid=1000(user) groups=1000(user),27(sudo),30(dip),46(plugdev),100(users),114(lpadmin)
- Exit the remote shell when finished to close the SSH session cleanly.
user@host:~$ exit logout Connection to host.example.net closed.

Mohd Shakir Zakaria is a cloud architect with deep roots in software development and open-source advocacy. Certified in AWS, Red Hat, VMware, ITIL, and Linux, he specializes in designing and managing robust cloud and on-premises infrastructures.
