Seeing the “REMOTE HOST IDENTIFICATION HAS CHANGED” warning from an SSH client signals that the remote server's identity no longer matches what is stored locally. The message appears before any password or key authentication and blocks the connection to prevent silently talking to an unexpected host. Handling the warning correctly restores connectivity while still protecting against impersonated servers.
During an OpenSSH handshake, the client checks the server's host key fingerprint against entries stored in /home/user/.ssh/known_hosts (or the equivalent path for the current account). The first time a host is contacted, the client shows the fingerprint and, when accepted, saves it in that file for later checks. On later connections, any mismatch between the stored fingerprint and the server's current host key triggers the identification‑changed warning.
Host keys can change legitimately after a system reinstall, migration, or intentional regeneration, but the same symptom also appears during a man‑in‑the‑middle attack. Before removing or replacing any entry in known_hosts, the presented fingerprint must be compared with a trusted source such as a console session or administrator‑supplied value. The steps below assume a standard OpenSSH client on a Unix‑like system and focus on updating the stored key only after the new server identity is trusted.
Steps to fix Remote Host Identification Has Changed! warning in SSH:
- Open a terminal on the client system that is attempting the SSH connection.
- Attempt the SSH connection again so the client prints the full host key mismatch warning and the new fingerprint.
$ ssh host.example.net Pseudo-terminal will not be allocated because stdin is not a terminal. @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ @ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @ @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY! Someone could be eavesdropping on you right now (man-in-the-middle attack)! It is also possible that a host key has just been changed. The fingerprint for the ED25519 key sent by the remote host is SHA256:W8JdNBQbOLbfHYW4TeYr5i2x95TaTYG9MTc/q4FJZYc. Please contact your system administrator. Add correct host key in /home/user/.ssh/known_hosts to get rid of this message. Offending ED25519 key in /home/user/.ssh/known_hosts:3 remove with: ssh-keygen -f '/home/user/.ssh/known_hosts' -R 'host.example.net' Host key for host.example.net has changed and you have requested strict checking. Host key verification failed.
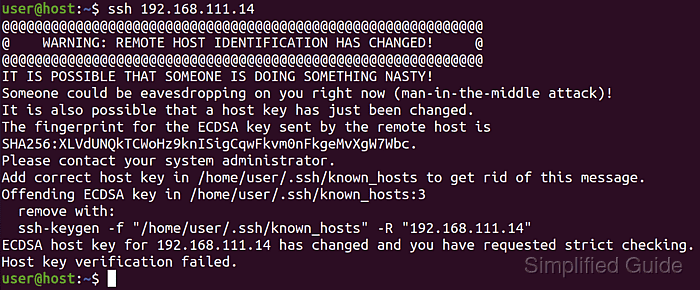
Proceed only after confirming that the host key change is expected, because trusting an unverified key allows a man-in-the-middle attacker to impersonate the server.
- Verify the new host key fingerprint using a trusted channel such as a console login on the server or information from an administrator.
# ssh-keygen -lf /etc/ssh/ssh_host_ed25519_key.pub 256 SHA256:W8JdNBQbOLbfHYW4TeYr5i2x95TaTYG9MTc/q4FJZYc root@host (ED25519)
This example command is run on the server to display the canonical host key fingerprint for comparison.
- Remove the outdated host key entry from the /home/user/.ssh/known_hosts file using the hostname or IP address shown in the warning.
$ ssh-keygen -R host.example.net # Host host.example.net found: line 1 # Host host.example.net found: line 2 # Host host.example.net found: line 3 /home/user/.ssh/known_hosts updated. Original contents retained as /home/user/.ssh/known_hosts.old
The warning output shows the exact file path and line number that must be removed.
- Optionally open /home/user/.ssh/known_hosts in a text tool to confirm the obsolete entry is gone and to clean up any duplicate hostnames or IP addresses.
$ sed -n '1,3p' ~/.ssh/known_hosts |1|cItuAnAS53f9L5UdyzHvuwNw614=|cMRAX1oGDH19k66i1utNWEf0F+k= ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIPiSpOwcjMn1M3OYhM1ARTZW6FUPBOFWnc1OT7riIsQP
Removing stale or duplicate lines avoids future confusion when a host is reachable by multiple names or addresses.
- Reconnect to the host so the client can store the trusted host key after confirming that the fingerprint matches the reference value.
$ ssh host.example.net hostname Warning: Permanently added 'host.example.net' (ED25519) to the list of known hosts. host
Type yes only when the fingerprint exactly matches the trusted value obtained earlier.
- Confirm that subsequent connections complete without the identification‑changed warning and proceed directly to authentication.
$ ssh user@host.example.net hostname host

Mohd Shakir Zakaria is a cloud architect with deep roots in software development and open-source advocacy. Certified in AWS, Red Hat, VMware, ITIL, and Linux, he specializes in designing and managing robust cloud and on-premises infrastructures.
