Enabling or disabling X11 forwarding on an SSH server controls whether graphical applications from a remote host can display on a local workstation through an encrypted session, supporting use of administrative tools and other GUI programs without exposing full desktop sharing.
In OpenSSH, X11 forwarding is governed primarily by the X11Forwarding directive in the server configuration file /etc/ssh/sshd_config. When forwarding is enabled, sshd creates an X11 proxy display, adjusts the DISPLAY and XAUTHORITY environment variables for the session, and tunnels all X11 traffic through the existing SSH connection instead of using a direct network link.
Changing this behavior affects both usability and security, because forwarded displays can provide a path for keystroke capture or interaction with local GUI applications if a client is compromised. Any modification of X11Forwarding should consider host hardening requirements and access patterns, and should always be paired with a configuration validation step before restarting sshd. On a typical Linux system, OpenSSH under systemd stores its server configuration in /etc/ssh/sshd_config and requires administrative access via sudo or a root shell to adjust these settings safely.
Steps to deny or allow X11 forwarding in SSH server:
- Open a terminal on the Linux server with access to sudo privileges.
$ whoami user
- Open the SSH server configuration file /etc/ssh/sshd_config in a text editor as root.
$ sudo vi /etc/ssh/sshd_config
- Locate any existing X11Forwarding directive lines in the configuration file.
$ grep -n "X11Forwarding" /etc/ssh/sshd_config 99:X11Forwarding yes 128:# X11Forwarding no
- Set X11Forwarding to yes to enable forwarding or to no to disable it.
X11Forwarding yes
Add the directive if missing and remove # from the beginning of the line if present.
- Save the changes to the configuration file in the text editor.
- Exit the text editor to return to the shell prompt.
- Test the sshd configuration for syntax errors before restarting the service.
$ sudo sshd -t
Restarting sshd with an invalid configuration can prevent new remote logins until access is restored through a console or other recovery method.
- Restart the sshd service to apply the updated X11 forwarding setting.
$ sudo systemctl restart ssh
- Verify the effective X11 forwarding setting reported by sshd.
$ sudo sshd -T | grep x11forwarding x11forwarding yes
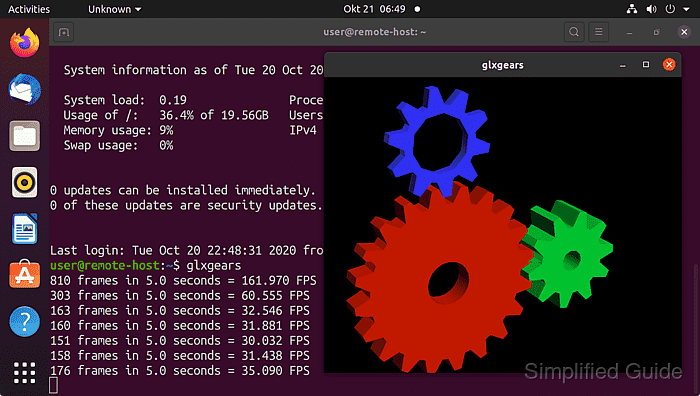
- Test X11 forwarding from a client by checking that the forwarded display is set.
$ ssh -X user@host.example.net "echo $DISPLAY" localhost:10.0
Successful X11 forwarding sets a localhost:N.0 display value that GUI applications use for rendering.

Mohd Shakir Zakaria is a cloud architect with deep roots in software development and open-source advocacy. Certified in AWS, Red Hat, VMware, ITIL, and Linux, he specializes in designing and managing robust cloud and on-premises infrastructures.
