Controlling which authentication methods an SSH server accepts reduces the attack surface and limits how accounts can be used. Disabling public key authentication can temporarily force password-only access, isolate compromised keys, or align access with stricter compliance requirements.
OpenSSH implements several authentication mechanisms, including public key, password, and keyboard-interactive methods. The server-side sshd daemon reads its configuration from /etc/ssh/sshd_config, where directives such as PubkeyAuthentication and PasswordAuthentication determine which methods are allowed when clients attempt to connect.
Changing authentication methods always carries a risk of losing access if no valid method remains enabled. Before disabling public key authentication, at least one alternative method such as strong password authentication or multi-factor integration must remain available, and some form of out-of-band or console access should be ready to reverse the change if needed.
PubkeyAuthentication
Specifies whether public key authentication is allowed in OpenSSH. The default value is yes.
Steps to disable SSH public key authentication:
- Open a terminal and connect to the SSH server with an account that can run sudo commands.
$ ssh user@host.example.net
- Create a backup copy of the current SSH daemon configuration file.
$ sudo cp /etc/ssh/sshd_config /etc/ssh/sshd_config.bak
An incorrect change in /etc/ssh/sshd_config without a backup can make new SSH logins fail and complicate rollback, especially on remote-only systems.
- Open the SSH daemon configuration file in a text editor.
$ sudo vi /etc/ssh/sshd_config [sudo] password for user:
- Search in the file for a line that begins with PubkeyAuthentication.
The directive may be commented as #PubkeyAuthentication yes in default configurations, in which case the effective value comes from the built-in default.
- Set the PubkeyAuthentication directive so public key authentication is disabled.
PubkeyAuthentication no
Add the line if it does not exist and remove any leading # so the directive is active.
- Confirm that at least one alternative authentication method such as PasswordAuthentication remains enabled.
PasswordAuthentication yes
Disabling PubkeyAuthentication while also disabling all other authentication methods prevents new sessions from authenticating and can completely block remote access.
- Test the sshd configuration for syntax errors before applying the change.
$ sudo sshd -t
No output from sshd -t indicates that the configuration syntax is valid.
- Restart the SSH daemon to apply the updated authentication policy.
$ sudo systemctl restart ssh
On many Debian-based systems the service name is ssh, while RHEL variants use sshd.
- Check the SSH daemon status to confirm that it is running after the restart.
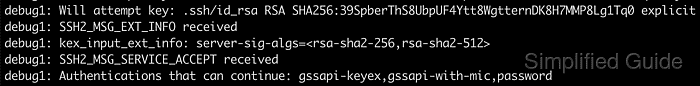
$ sudo systemctl status ssh ● ssh.service - OpenBSD Secure Shell server Loaded: loaded (/usr/lib/systemd/system/ssh.service; enabled; preset: enabled) Active: active (running) since Sat 2026-01-10 12:25:56 +08; 17s ago TriggeredBy: ● ssh.socket Docs: man:sshd(8) man:sshd_config(5) Process: 12946 ExecStartPre=/usr/sbin/sshd -t (code=exited, status=0/SUCCESS) Main PID: 12953 (sshd) Tasks: 1 (limit: 4546) Memory: 1.1M (peak: 1.4M) CPU: 11ms CGroup: /system.slice/ssh.service └─12953 \"sshd: /usr/sbin/sshd -D [listener] 0 of 10-100 startups\" ##### snipped ##### - Verify that public key authentication is no longer accepted and that another method remains available by initiating a verbose SSH connection and reviewing the offered methods.
$ ssh -vv user@host.example.net ##### snipped ##### debug1: Authentications that can continue: password ##### snipped #####
The absence of publickey in the list of methods that can continue shows that public key authentication is disabled; a remaining method such as password must still be present to allow logins.

Mohd Shakir Zakaria is a cloud architect with deep roots in software development and open-source advocacy. Certified in AWS, Red Hat, VMware, ITIL, and Linux, he specializes in designing and managing robust cloud and on-premises infrastructures.
