Recovering the GRUB bootloader restores control over system startup when a machine stops presenting the expected boot menu or begins booting directly into another operating system. The bootloader coordinates the transfer of control from BIOS or UEFI firmware to installed kernels, so damage to its code or configuration can leave Linux installations hidden behind another loader such as Windows Boot Manager. Reinstalling GRUB to the system disk restores the selector that exposes all available operating systems without reinstalling them.
On most Linux systems, GRUB stores its core modules and configuration under /boot and /boot/grub while a small first-stage loader resides either in the disk's master boot record or in an EFI system partition. Booting from a compatible Linux Live CD or USB drive makes it possible to mount the installed root filesystem and access these directories even when the normal boot process fails. Using chroot from the live environment causes tools such as grub-install and update-grub to operate on the mounted system instead of the temporary live root.
The procedure assumes a single-disk setup that uses GRUB as the primary bootloader, with examples based on a typical Ubuntu live session. Systems using multiple disks, complex RAID layouts, encrypted volumes, or custom UEFI configurations may require adjusted device names and additional mount steps for locations such as /boot/efi. Careful disk identification is critical because writing GRUB to the wrong drive can overwrite another bootloader or leave a system unbootable until corrected.
Steps to restore GRUB bootloader:
- Boot the computer from a Linux Live CD or USB drive that matches the installed system's architecture.
- Select the live desktop session instead of starting an installer.
For Ubuntu installation media, click the Try Ubuntu button to start a live session.
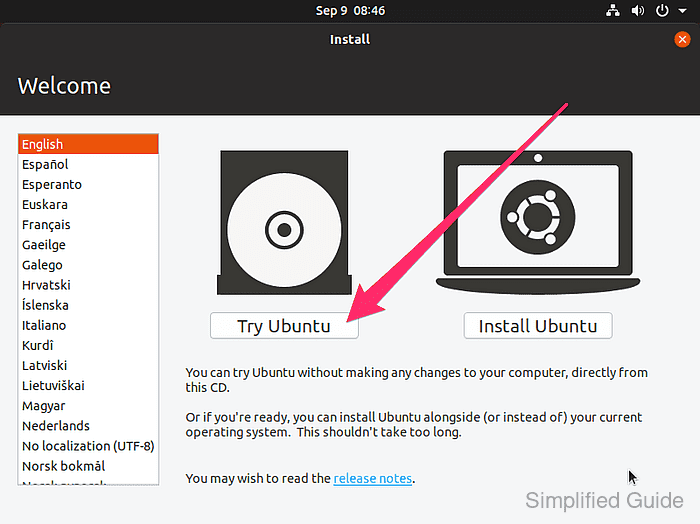
- Open a terminal in the live environment.
If no graphical session is available, press <ctrl> + <alt> + <f2> to reach a TTY and log in as ubuntu with an empty password when using Ubuntu live media.
- List block devices to locate the disk and partition containing the installed Linux system.
$ lsblk NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINTS loop0 7:0 0 512M 0 loop /mnt/bench loop1 7:1 0 64M 0 loop loop2 7:2 0 32M 0 loop loop3 7:3 0 128M 0 loop /mnt/grub-test loop4 7:4 0 128M 0 loop /mnt/grub-test loop5 7:5 0 128M 0 loop /mnt/grub-recover nbd0 43:0 0 0B 0 disk nbd1 43:32 0 0B 0 disk nbd2 43:64 0 0B 0 disk nbd3 43:96 0 0B 0 disk nbd4 43:128 0 0B 0 disk nbd5 43:160 0 0B 0 disk nbd6 43:192 0 0B 0 disk nbd7 43:224 0 0B 0 disk vda 254:0 0 1.8T 0 disk `-vda1 254:1 0 1.8T 0 part /etc/hosts /etc/hostname /etc/resolv.conf vdb 254:16 0 606.5M 1 disk nbd8 43:256 0 0B 0 disk nbd9 43:288 0 0B 0 disk nbd10 43:320 0 0B 0 disk nbd11 43:352 0 0B 0 disk nbd12 43:384 0 0B 0 disk nbd13 43:416 0 0B 0 disk nbd14 43:448 0 0B 0 disk nbd15 43:480 0 0B 0 diskFocus on the main system disk such as /dev/sda and identify the root partition by its size and filesystem type, typically an ext4 partition.
- Create a temporary directory for mounting the root filesystem from the installed system.
$ mkdir -p /mnt/grub-recover
Any directory name is acceptable; using a dedicated directory keeps the remaining commands short.
- Mount the root partition of the installed Linux system into the temporary directory.
$ sudo mount /dev/loop5 /mnt/grub-recover
Mount the correct root partition; reinstalling GRUB against the wrong filesystem can attach the bootloader to an unexpected installation.
- Bind essential virtual filesystems from the live environment into the mounted root.
$ sudo mount --bind /dev /mnt/grub-recover/dev $ sudo mount --bind /proc /mnt/grub-recover/proc $ sudo mount --bind /sys /mnt/grub-recover/sys $ sudo mount --bind /bin /mnt/grub-recover/bin $ sudo mount --bind /lib /mnt/grub-recover/lib $ sudo mount --bind /usr /mnt/grub-recover/usr $ sudo mount --bind /etc /mnt/grub-recover/etc
Binding /dev, /proc, and /sys ensures tools inside the chroot see devices, kernel information, and firmware interfaces correctly.
- Reinstall the GRUB bootloader to the primary disk used by the system firmware.
$ sudo chroot /mnt/grub-recover /bin/bash -c "grub-install --target=arm64-efi --efi-directory=/boot/efi --boot-directory=/boot --removable" Installing for arm64-efi platform. grub-install: error: /boot/efi doesn't look like an EFI partition.
Ensure the correct disk such as /dev/sda is targeted; installing GRUB to the wrong drive can overwrite another bootloader and temporarily prevent other operating systems from starting.
- Regenerate the GRUB configuration file to detect installed kernels and other operating systems.
$ sudo chroot /mnt/grub-recover /bin/bash -c "update-grub" Sourcing file `/etc/default/grub' Generating grub configuration file ... Warning: os-prober will be executed to detect other bootable partitions. Its output will be used to detect bootable binaries on them and create new boot entries. Adding boot menu entry for UEFI Firmware Settings ... done
On distributions without update-grub, use grub-mkconfig -o /boot/grub/grub.cfg to generate the configuration.
- Exit from the chroot environment back to the live session.
- Power off the machine from the live environment.
- Remove the Live CD or USB drive from the system.
- Boot the computer from the primary disk that now holds the recovered GRUB bootloader.
- Verify that the GRUB menu appears and that at least one installed operating system starts successfully.

Mohd Shakir Zakaria is a cloud architect with deep roots in software development and open-source advocacy. Certified in AWS, Red Hat, VMware, ITIL, and Linux, he specializes in designing and managing robust cloud and on-premises infrastructures.
