Inspecting the routing table on Linux clarifies how packets leave and enter a host by showing default gateways, directly attached networks, and special routes. Clear visibility of these entries helps explain unreachable subnets, asymmetric paths, and policy decisions that affect latency and resilience.
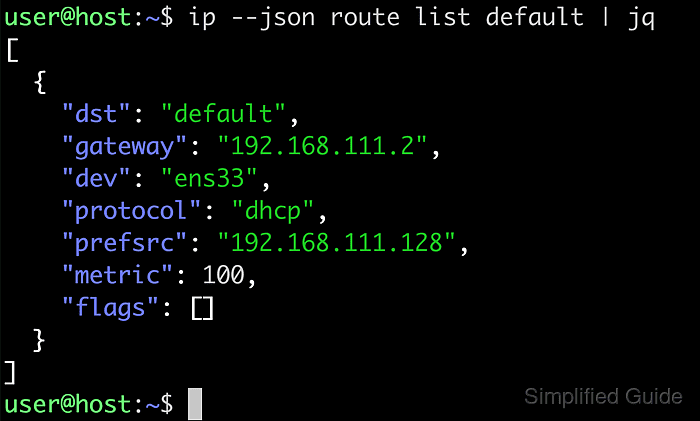
The kernel stores routing information in the Routing Information Base (RIB) and consults it for every outgoing packet. Tools from the iproute2 suite, particularly the ip route subcommand, query and manipulate this data, exposing tables such as main and local for IPv4 and IPv6 with destinations, next-hop gateways, interface names, and metrics.
Complex topologies that involve multiple interfaces, VPNs, containers, or policy-based routing can introduce overlapping or custom tables, so interpreting entries depends on accurate knowledge of interface names and address plans. Some commands may require elevated privileges, and changes made interactively are typically ephemeral unless duplicated in configuration files such as /etc/netplan, /etc/network/interfaces, NetworkManager profiles, or distribution-specific network scripts.
Related: How to check the default route in Linux
Related: How to add a static route in Linux
Steps to check the routing table in Linux:
- Open a terminal with access to an account that can run administrative commands if required.
- Display the full IPv4 routing table using the ip route command.
$ ip route default via 192.0.2.1 dev eth0 proto dhcp src 192.0.2.40 metric 100 192.0.2.0/24 dev eth0 proto kernel scope link src 192.0.2.40 metric 100 192.0.2.1 dev eth0 proto dhcp scope link src 192.0.2.40 metric 100

The base form ip route shows routes from the main table, including the default gateway and connected networks.
- Show only default routes to identify the primary gateway in use.
$ ip route show default default via 192.0.2.1 dev eth0 proto dhcp src 192.0.2.40 metric 100 $ ip route | grep ^default default via 192.0.2.1 dev eth0 proto dhcp src 192.0.2.40 metric 100
Filtering with grep gives a quick view of default routes when the table contains many entries.
- Inspect routes for a specific destination prefix or host address to see the chosen interface and next hop.
$ ip route show 192.0.2.0/24 192.0.2.0/24 dev eth0 proto kernel scope link src 192.0.2.40 metric 100 $ ip route get 203.0.113.50 203.0.113.50 via 192.0.2.1 dev eth0 src 192.0.2.40 uid 0 cacheReplace the sample prefix or address with the network or host under investigation to confirm which path the kernel will select.
- Display IPv6 routing information if IPv6 connectivity is configured on the system.
$ ip -6 route fe80::/64 dev eth0 proto kernel metric 256 pref medium
IPv6 routes follow the same lookup logic as IPv4 but use IPv6 prefixes and can appear in separate tables managed by iproute2.
- Verify routing behaviour by sending a few echo requests through the default route to a known reachable host.
$ ping -c 3 203.0.113.50 PING 203.0.113.50 (203.0.113.50) 56(84) bytes of data. 64 bytes from 203.0.113.50: icmp_seq=1 ttl=128 time=4.26 ms 64 bytes from 203.0.113.50: icmp_seq=2 ttl=128 time=4.49 ms 64 bytes from 203.0.113.50: icmp_seq=3 ttl=128 time=4.68 ms --- 203.0.113.50 ping statistics --- 3 packets transmitted, 3 received, 0% packet loss, time 2013ms rtt min/avg/max/mdev = 4.255/4.474/4.683/0.174 ms
Successful replies confirm that the active routes and default gateway provide functional connectivity to external networks.

Mohd Shakir Zakaria is a cloud architect with deep roots in software development and open-source advocacy. Certified in AWS, Red Hat, VMware, ITIL, and Linux, he specializes in designing and managing robust cloud and on-premises infrastructures.
