Changing the UUID of a disk or partition prevents conflicts when disks are cloned, swapped between machines, or attached alongside similar layouts. A unique identifier also keeps mount points stable when device names such as sda1 or sdb1 change after hardware modifications.
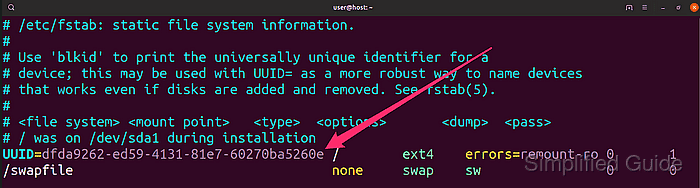
On Linux systems, mount configuration usually refers to partitions by UUID in /etc/fstab instead of by device name. The kernel and systemd read these identifiers during boot, match them to block devices, and mount filesystems at their configured locations.
Changing a filesystem identifier affects any configuration that refers to the old value, especially entries in /etc/fstab and bootloaders that rely on specific UUIDs. The procedure requires unmounting the filesystem, validating its integrity, assigning the new UUID, and updating configuration files to avoid unmountable filesystems or failed boots.
Steps to change disk or partition UUID in Linux:
- Open a terminal with sudo privileges.
$ whoami user
- List block devices and locate the target partition by name, filesystem type, and existing UUID.
$ lsblk -f NAME FSTYPE FSVER LABEL UUID FSAVAIL FSUSE% MOUNTPOINTS ##### snipped ##### loop0 ├─loop0p1 ext4 1.0 data ed6aa5ab-3a4d-43bd-b7d2-ffec8c1d0291 /root/disk ├─loop0p2 94.9M 0% /mnt/uuidtest └─loop0p3 ext4 1.0 uuiddemo bea29d1f-abb8-4ed3-acd6-273280d2f4ba 205.8M 0% /mnt/uuiddemo loop1 ext4 1.0 data e2509569-0ada-480b-833e-797ee7ca99f1 sda ├─sda1 vfat FAT32 F410-21AB 1G 1% /boot/efi ├─sda2 ext4 1.0 92df6435-4bce-455b-9dff-2f517721e1d7 1.6G 10% /boot └─sda3 LVM2_member LVM2 001 nsoAwu-bMdN-ebGG-jbKp-I2Kp-tkHr-s2gz0z ##### snipped #####
lsblk with the -f option shows filesystem type, label, and UUID for each partition.
- Generate a new UUID value for the filesystem.
$ uuidgen 3d16b3cc-f0f4-43ee-9cb6-c0fd54229a81
uuidgen is normally installed by default on most Linux systems.
Another random UUID can be read from /proc/sys/kernel/random/uuid.
$ cat /proc/sys/kernel/random/uuid 3907fd6b-dfca-48c6-9baa-84cc1719e9ba
- Unmount the filesystem on the target partition so it can be modified safely.
$ sudo umount /dev/loop0p3
Replace loop0p3 with the actual partition identifier discovered in the listing step.
- Check the filesystem for errors before changing the UUID.
$ sudo e2fsck -fy /dev/loop0p3 e2fsck 1.47.0 (5-Feb-2023) Pass 1: Checking inodes, blocks, and sizes Pass 2: Checking directory structure Pass 3: Checking directory connectivity Pass 4: Checking reference counts Pass 5: Checking group summary information uuiddemo: 11/65536 files (0.0% non-contiguous), 8268/65536 blocks
This step ensures the filesystem is consistent before applying a new UUID.
- Assign the new UUID value to the ext* filesystem with tune2fs.
$ sudo tune2fs -U 3d16b3cc-f0f4-43ee-9cb6-c0fd54229a81 /dev/loop0p3 tune2fs 1.47.0 (5-Feb-2023)
tune2fs operates only on ext2, ext3, and ext4 filesystems; other types such as XFS or Btrfs require tools like xfs_admin or btrfs filesystem label for equivalent operations.
- Confirm that the partition now reports the new UUID.
$ sudo blkid /dev/loop0p3 /dev/loop0p3: LABEL="uuiddemo" UUID="3d16b3cc-f0f4-43ee-9cb6-c0fd54229a81" BLOCK_SIZE="4096" TYPE="ext4" PARTLABEL="primary" PARTUUID="e9b64fa3-a8b8-4c91-b8a8-fad4fb897c8f"
- Update the matching entry in /etc/fstab so that it references the new UUID for the partition.
$ sudoedit /etc/fstab
/etc/fstab UUID=3d16b3cc-f0f4-43ee-9cb6-c0fd54229a81 /mnt/uuiddemo ext4 defaults 0 2 ##### snipped #####
Incorrect /etc/fstab entries can prevent the system from booting if they affect root or other essential filesystems.
- Reload fstab-controlled mounts to apply the updated configuration.
$ sudo mount -a
No output typically indicates that all mounts defined in /etc/fstab succeeded.
- Verify that the partition is mounted as expected with the new UUID.
$ findmnt /dev/loop0p3 TARGET SOURCE FSTYPE OPTIONS /mnt/uuiddemo /dev/loop0p3 ext4 rw,relatime

Mohd Shakir Zakaria is a cloud architect with deep roots in software development and open-source advocacy. Certified in AWS, Red Hat, VMware, ITIL, and Linux, he specializes in designing and managing robust cloud and on-premises infrastructures.
