Directing Linux terminal traffic through an HTTP or HTTPS proxy enables access to remote services from restricted networks and centralizes outbound control. A proxy can mask client IP addresses, support logging and filtering, and enforce organizational security policies for command-line tools.
On Linux, many command-line applications read proxy configuration from environment variables such as http_proxy and https_proxy. These variables hold complete proxy URLs, including scheme, host, port, and optional credentials, and are honored by utilities like curl, wget, and common package managers without separate per-application settings.
Incorrect or overly broad proxy values can disrupt connectivity, expose credentials in shell history or configuration files, or route traffic through unintended intermediaries. A reachable proxy server, suitable authentication details, and a deliberate choice between per-session, per-user, or system-wide configuration form the main prerequisites for safely configuring proxies for terminal applications.
Steps to configure HTTP and HTTPS proxy on Linux:
- Set up a proxy server if none is available.
- Open a terminal on the Linux system.
- Check whether any HTTP or HTTPS proxy is currently in use by querying the external IP address (optional).
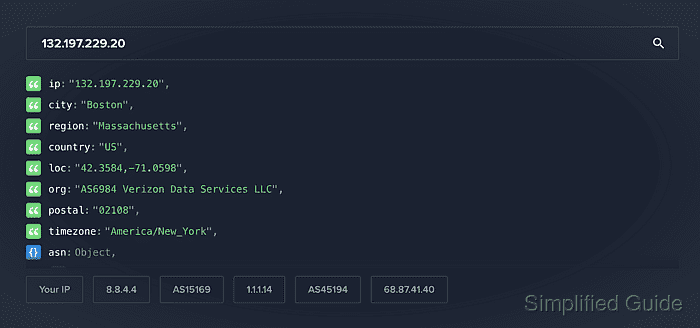
$ curl --silent https://ipinfo.io { "ip": "60.50.201.170", "hostname": "170.201.50.60.cbj04-home.tm.net.my", "city": "Cyberjaya", "region": "Selangor", "country": "MY", "loc": "2.9228,101.6572", "org": "AS4788 TM TECHNOLOGY SERVICES SDN. BHD.", "postal": "63100", "timezone": "Asia/Kuala_Lumpur", "readme": "https://ipinfo.io/missingauth" }Related: How to install cURL on Ubuntu
With a working Internet connection, the output displays the gateway or upstream router IP details.
Example terminal tools that honor proxy variables include curl, wget, ftp, ssh, yum and apt.
- Verify which proxy environment variables are set in the current terminal session.
$ echo $http_proxy $https_proxy $HTTP_PROXY $HTTPS_PROXY
No proxy is configured when the command prints empty output.
http_proxy and https_proxy are the standard variables, while HTTP_PROXY and HTTPS_PROXY are uppercase equivalents. The ftp_proxy environment variable can be used to route FTP traffic through a proxy.
- Configure the http_proxy and https_proxy environment variables for the current session.
$ export http_proxy="http://proxy.example.net:8888" $ export https_proxy="http://proxy.example.net:8888"
General format for authenticated proxies:
<TYPE>://<USERNAME>:<PASSWORD>@<IP_OR_HOSTNAME>:<PORT>
Omit credentials when authentication is not required, for example:
$ export https_proxy="http://proxy.example.net:8888"
Common proxy schemes include http, https, socks4 and socks5.
- Export uppercase proxy variables for applications that expect them (optional).
$ export HTTP_PROXY="$http_proxy" $ export HTTPS_PROXY="$https_proxy"
Some tools only consult HTTP_PROXY and HTTPS_PROXY and ignore the lowercase variants.
- Persist the proxy configuration for every new Bash session of the current user (optional).
$ echo 'export http_proxy="http://proxy.example.net:8888"' >> ~/.bashrc $ echo 'export https_proxy="http://proxy.example.net:8888"' >> ~/.bashrc
~/.bashrc is executed for each new interactive Bash terminal session. ~/.zshrc is the corresponding file for Zsh and can contain the same export lines.
Incorrect edits to shell startup files can cause new terminals to start with errors or unexpected environment settings.
- Persist the proxy configuration for all system users through the global profile (optional).
$ echo 'export http_proxy="http://proxy.example.net:8888"' | sudo tee --append /etc/profile export http_proxy="http://proxy.example.net:8888" $ echo 'export https_proxy="http://proxy.example.net:8888"' | sudo tee --append /etc/profile export https_proxy="http://proxy.example.net:8888"
/etc/profile is evaluated for many login shells, so changes here affect all users and service accounts that source this file.
- Confirm that the proxy environment variables are set to the expected values.
$ echo $https_proxy $http_proxy http://proxy.example.net:8888 http://proxy.example.net:8888
Open a new terminal after modifying /etc/profile or ~/.bashrc so the updated configuration is loaded.
- Test that terminal applications now use the proxy server by checking the external IP again.
$ curl --silent https://ipinfo.io { "ip": "60.50.201.170", "hostname": "170.201.50.60.cbj04-home.tm.net.my", "city": "Cyberjaya", "region": "Selangor", "country": "MY", "loc": "2.9228,101.6572", "org": "AS4788 TM TECHNOLOGY SERVICES SDN. BHD.", "postal": "63100", "timezone": "Asia/Kuala_Lumpur", "readme": "https://ipinfo.io/missingauth" }If the proxy uses the same upstream connection as the client, the reported IP may remain unchanged even though traffic is routed through the proxy.
- Remove proxy settings from the current session when direct connectivity is required.
$ unset http_proxy https_proxy HTTP_PROXY HTTPS_PROXY
Any export lines added to ~/.bashrc, ~/.zshrc or /etc/profile must be removed to prevent future sessions from inheriting the proxy configuration.

Mohd Shakir Zakaria is a cloud architect with deep roots in software development and open-source advocacy. Certified in AWS, Red Hat, VMware, ITIL, and Linux, he specializes in designing and managing robust cloud and on-premises infrastructures.
