To manage AWS services through command-line tools, it is necessary to create a programmatic access user in AWS Identity and Access Management (IAM). This type of user is provided with an AWS Access Key ID and an AWS Secret Access Key. These credentials enable interaction with AWS services without using the AWS Management Console.
Creating a programmatic access user involves defining the user's permissions in IAM and generating access keys. These access keys are critical for authentication and ensuring that commands executed via AWS CLI are authorized.
Properly configuring programmatic access users is essential for securing your AWS environment. Handling and rotating access keys should be done with care to maintain security and control over your AWS resources.
Related: How to configure the AWS CLI
Steps to create a programmatic access user in AWS IAM:
- Go to IAM section in your AWS Console.
Related: Identity and Access Management
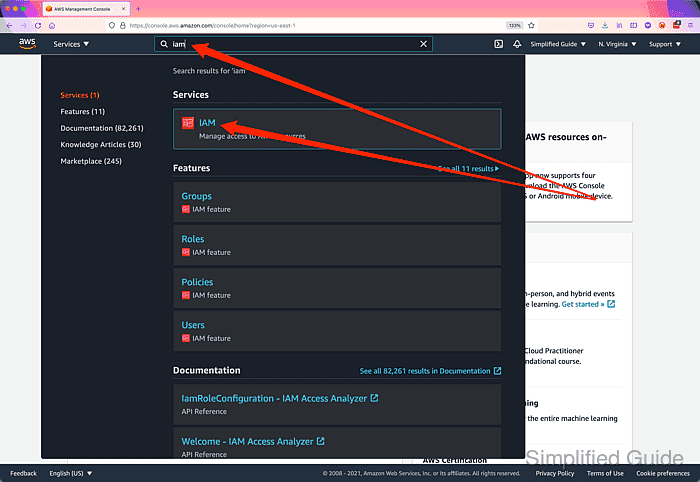
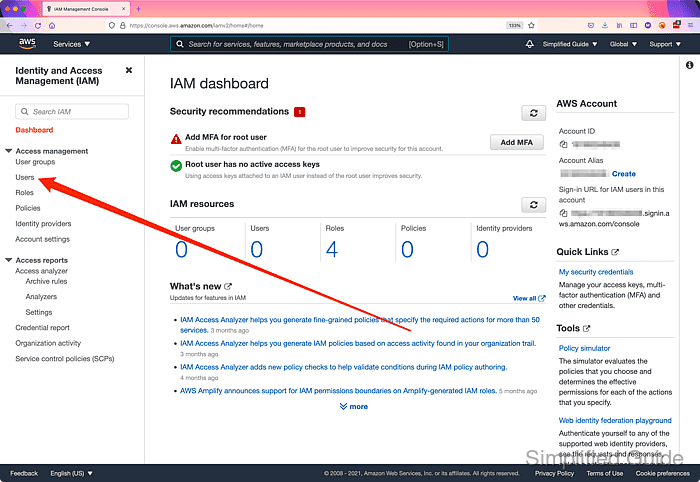
- Click on the Users link on the sidebar.
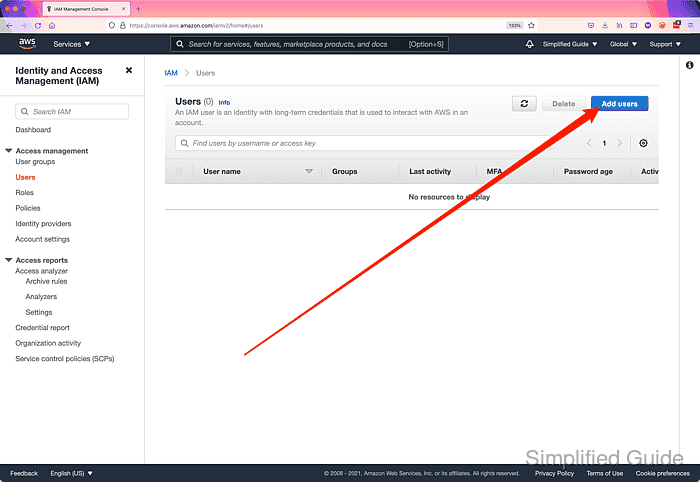
- Click on the Add user button to add a new user.
- Enter User name for the user.
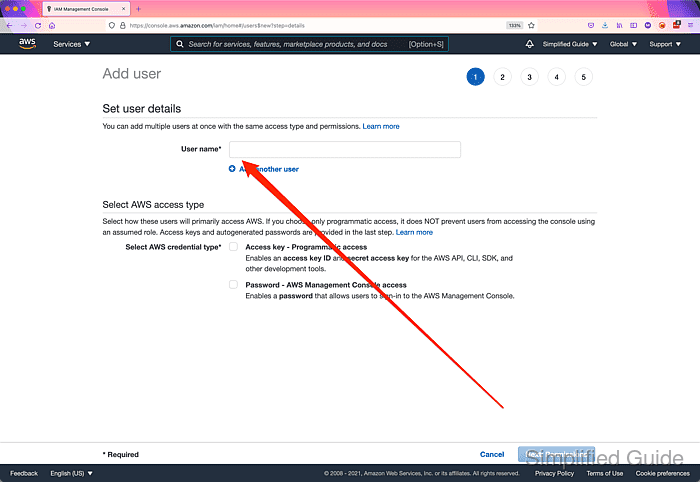
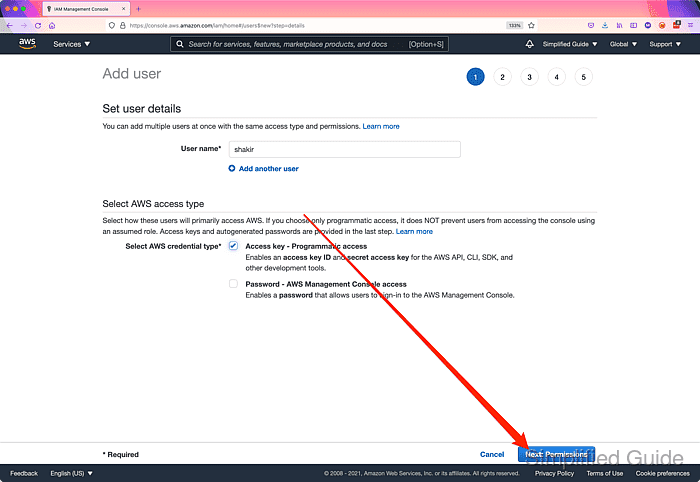
- Tick on Access key - Programmatic access checkbox in Access type section.
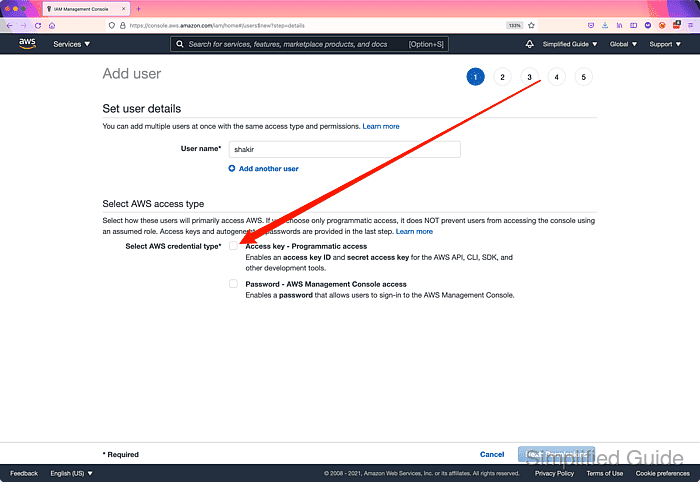
- Click on the Next: Permissions button.
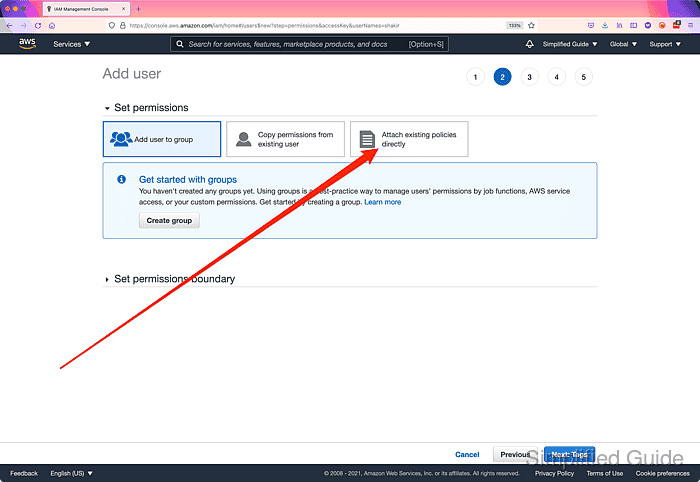
- Configure access or permission for the user.
You choose any of the available methods to assign permissions to the user, but we'll be using the Attach Existing policies directly method in this example.
- Click on Attach Existing policies directly tab.
- Tick on the checkbox of the access policies that you want to assign to the user.
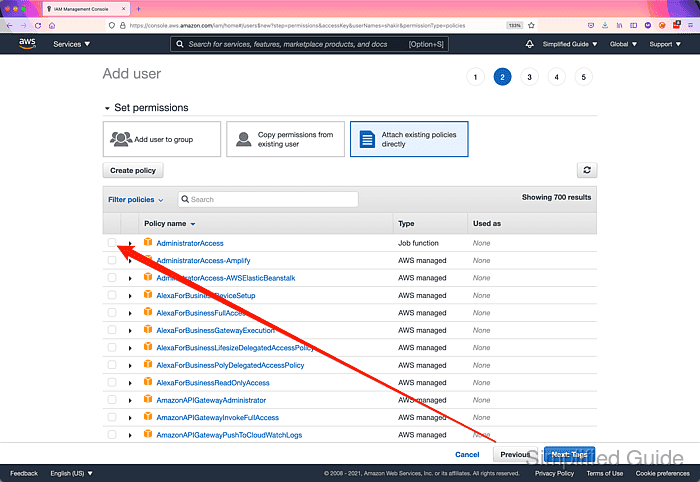
- Click on the Next: Tags button.
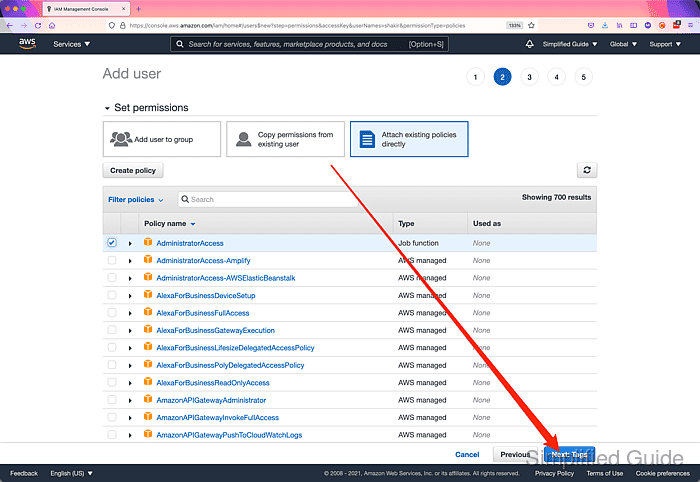
- Add tags to the user (optional) and click on Next: Review buttonw.
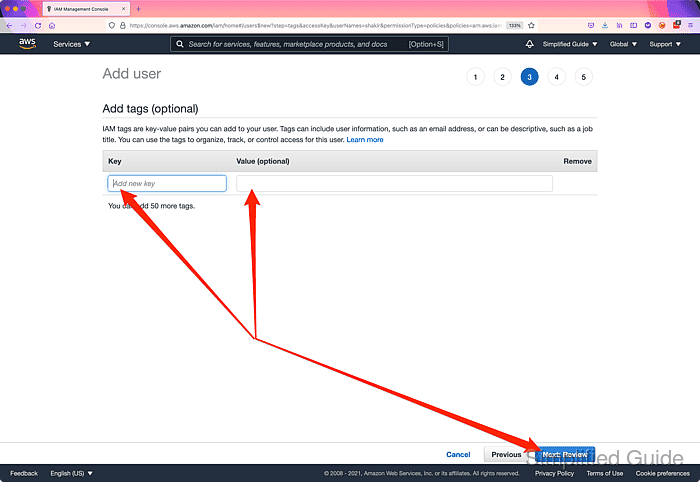
- Review the summary of the user and click on the Create user button.
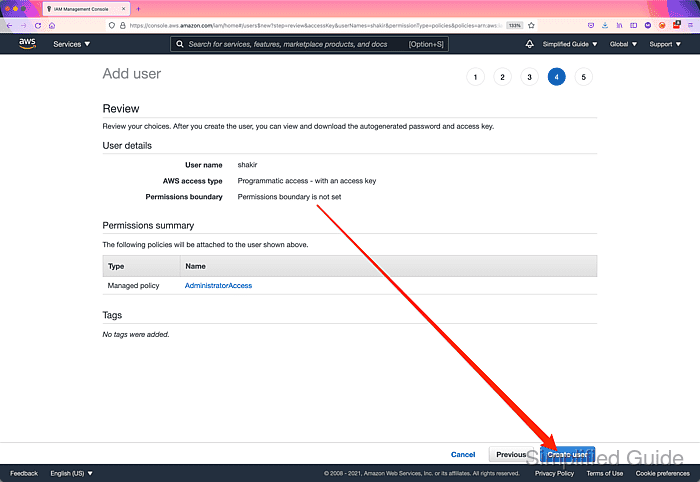
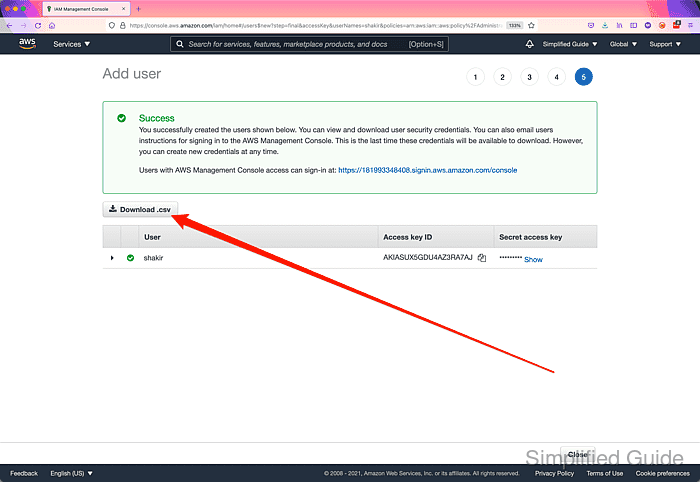
- Click Download .csv button to download the login details.
- Configure awscli using the details in the file downloaded csv file.
Related: How to configure the AWS CLI

Mohd Shakir Zakaria is a cloud architect with deep roots in software development and open-source advocacy. Certified in AWS, Red Hat, VMware, ITIL, and Linux, he specializes in designing and managing robust cloud and on-premises infrastructures.
