When you use AWS CLI, it automatically creates a default profile during the initial configuration. This profile contains the basic settings for accessing your AWS account. However, in scenarios where you need to manage multiple AWS accounts or environments, configuring multiple profiles is essential.
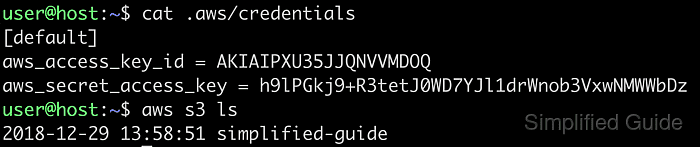
Creating multiple profiles, also known as named profiles, allows you to manage separate credentials and configurations for different AWS accounts or roles. You can switch between these profiles based on your needs without altering the global settings. This setup ensures that each profile operates independently, reducing the risk of accidental misconfigurations or unauthorized access.
To configure multiple profiles, use the aws configure command with the --profile option. This lets you specify different access keys, regions, and output formats for each profile. After setting up, you can select the appropriate profile when running AWS CLI commands, enabling efficient management of multiple accounts or environments.
Related: How to configure the AWS CLI
Related: How to switch profiles on AWS CLI
Steps to configure multiple AWS CLI profiles:
- Open your terminal or command prompt.
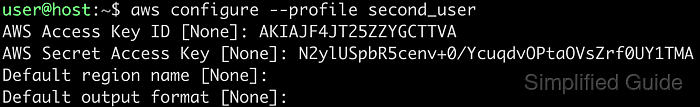
- Use the aws configure –profile [profile_name] command to create a new profile.
$ aws configure --profile second_user
- Enter your AWS Access Key ID when prompted.
AWS Access Key ID [None]: AKIAJF4JT25ZZYGCTTVA
- Enter your AWS Secret Access Key when prompted.
AWS Secret Access Key [None]: N2ylUSpbR5cenv+0/YcuqdvOPtaOVsZrf0UY1TMA
- Specify the Default region name for this profile.
Default region name [None]:
- Specify the Default output format if necessary.
Default output format [None]:
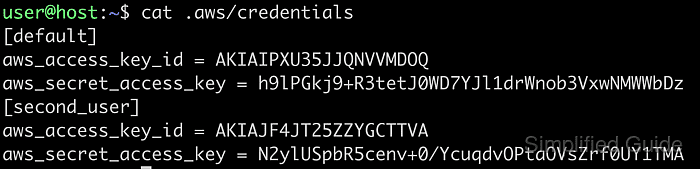
- Verify the configuration by checking the .aws/credentials file.
$ cat .aws/credentials [default] aws_access_key_id = AKIAIPXU35JJQNVVMDOQ aws_secret_access_key = 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 [second_user] aws_access_key_id = AKIAJF4JT25ZZYGCTTVA aws_secret_access_key = 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

Mohd Shakir Zakaria is a cloud architect with deep roots in software development and open-source advocacy. Certified in AWS, Red Hat, VMware, ITIL, and Linux, he specializes in designing and managing robust cloud and on-premises infrastructures.
